Privileged Access Management
and your Zero Trust journey
See why modern PAM should be the first step
on the road to Zero Trust security.
Challenge
You can’t rely on a network perimeter to separate trusted insiders from untrusted outsiders.
Risk
Standing privileges and broad access rights invite data breaches and cyber attacks.
Solution
Zero Trust reduces cyber risk and lowers the cost of a data breach by 42%, according to IBM.
What is Zero Trust Security?
Regulatory bodies, government agencies, and CIOs are mandating Zero Trust as a cyber security framework. What does Zero Trust mean for your security strategy?
With a Zero Trust security model, nobody is trusted automatically, even when they’ve cleared the perimeter. Instead, all identities are verified, minimum access is granted based on context, and activities are monitored to make sure controls are working as expected.

How do you achieve the Zero Trust vision?
The Zero Trust model requires multiple security controls throughout an IT environment to protect and manage identities, devices, networks, applications, and data.
PAM capabilities such as verifying identities, adopting Multi-Factor Authentication (MFA), and enforcing least privilege are essential capabilities to address Zero Trust challenges.
Read Zero Trust for Dummies to see how Delinea supports your journey to Zero Trust »

Redefining Legacy PAM
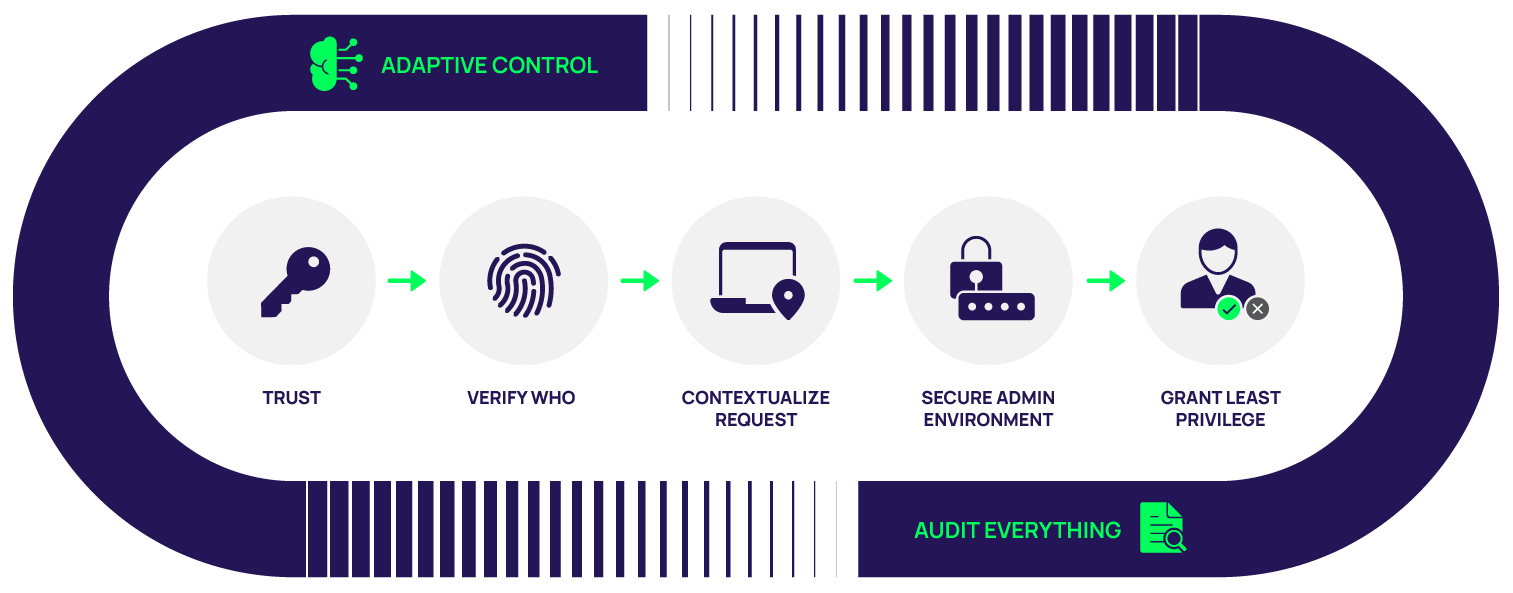
Verify who is requesting access
Zero Trust means moving from implicit trust when users are inside the network to explicit trust that is gained through increasing forms of verifying the user and their device.
Establish and manage unique, low-privilege identities for all users who require privileged access, including IT, business users, and applications and services. Enable just-in-time access via workflows and enforce MFA everywhere for identity assurance.
See how to manage identities in the cloud and on -premise with Server PAM »
Limit and secure privileged accounts
The lowest hanging fruit in the PAM world, and a great way to remove lots of risk quickly and easily, is vaulting shared privileged accounts and automatically rotating their passwords on a regular schedule.
PAM includes a centralized policy engine to manage all access requests and enforce approvals and governance throughout the lifecycle of privileged accounts. With PAM in place, you can reduce your attack surface by eliminating unnecessary shared privileged accounts and protect the ones you absolutely need in a secure vault.
See how Secret Server on the Delinea Platform manages privileged accounts »
Follow the principle of least privilege
To implement a Zero Trust security strategy never grant broad or standing privileges. Instead, provide only the needed level of privilege to perform specific tasks and only for the period necessary. Any privilege elevation must be approved and limited in time and scope.
Eliminating local admin accounts prevents installation of malicious software and lateral movement. It’s essential to provide only limited access for workstations as well as servers.>
See how to provide admins Zero Trust access to servers with Server PAM »
See how to provide business users Zero Trust access to workstations with Privilege Manager »
Monitor and audit everything
Continuous monitoring is a critical security control in a Zero Trust model. You must have oversight of all privileged user activity and be able to record, review, and document everything at a granular level.
PAM helps you improve accountability, conduct forensic investigations, and prove compliance with government regulations and industry mandates.
See how Secret Server on the Delinea Platform enables privileged session management »
See how Privileged Behavior Analytics detects anomalous behavior »
PAM Solutions for Zero Trust
Full-featured, free trials get you up and running fast
Secret Server
Discover privileged accounts, vault credentials, ensure password complexity, delegate access, and manage sessions.
Server PAM
Privilege Manager
Remove local admin rights and implement policy-based application control in a single solution.
Privileged Behavior Analytics
Increase accountability and oversight of privileged accounts.

Least Privilege Cybersecurity for Dummies
FREE EBOOK
The smart guide to jump-start your least privilege strategy. Get this free 16-page eBook to see how you can limit user and application access to privileged accounts—especially on endpoints—through various controls and tools without impacting productivity.
