Privileged Access Management
Maturity Model
A framework to help you systematically lower risk, increase
business agility, and improve operational efficiency.
Challenge
Identity and privilege-based attacks are increasing but you don’t have unlimited resources for defense.
Risk
Acting without a roadmap leads to unused investments, expensive rework, and a false sense of security.
Solution
Build the right PAM foundation to reduce cyber risk fast and grow seamlessly at your own pace.
The PAM Maturity Model
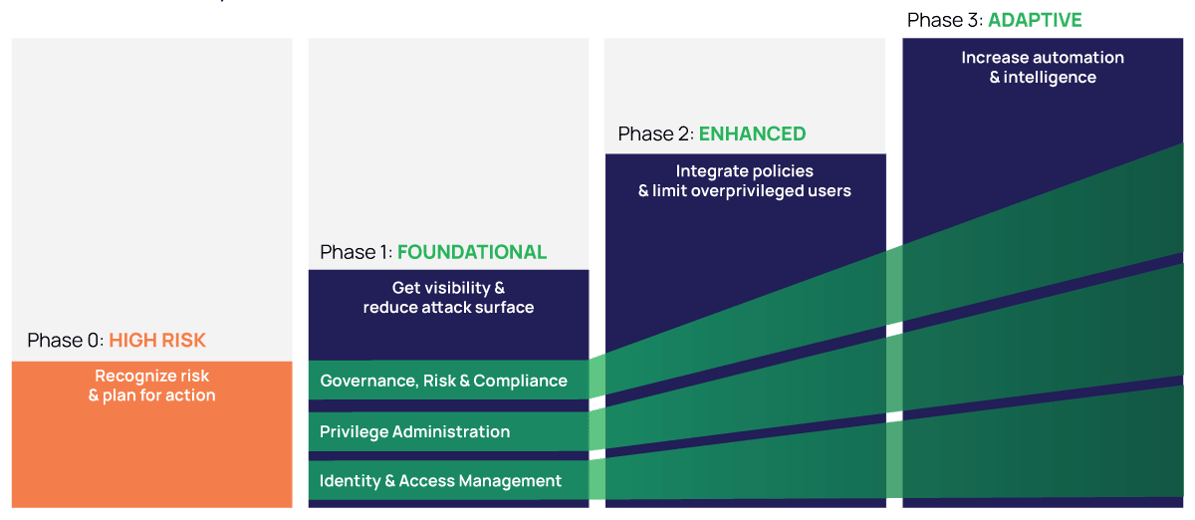
Step-by-step framework for reducing risk
Privileged Access Management (PAM) is the most effective way to combat identity and privilege-based attacks, by securing passwords and other secrets, granular access control, session management, and other Zero Trust strategies.
But, trying to implement all PAM capabilities at the same time would be a daunting project and cause friction for users.
Using this model, you can benchmark your current security practices, set your priorities, and build a roadmap to accelerate your PAM maturity.
Experiences from 10,000+ companies inform the maturity model
The model is based on security industry best practices and Delinea’s work with companies ranging from organizations just beginning their PAM journey to the most experienced. In each phase of PAM maturity:
Scope expands to include more types of privileged users, systems, and accounts.
Intelligence and automation increase so your PAM system is continuously learning and adapting.
Controls become more granular and dynamic to govern, validate, and automate access.
Integrations embed PAM in your workflows so PAM becomes virtually invisible to most users.
PAM maturity is multi-dimensional
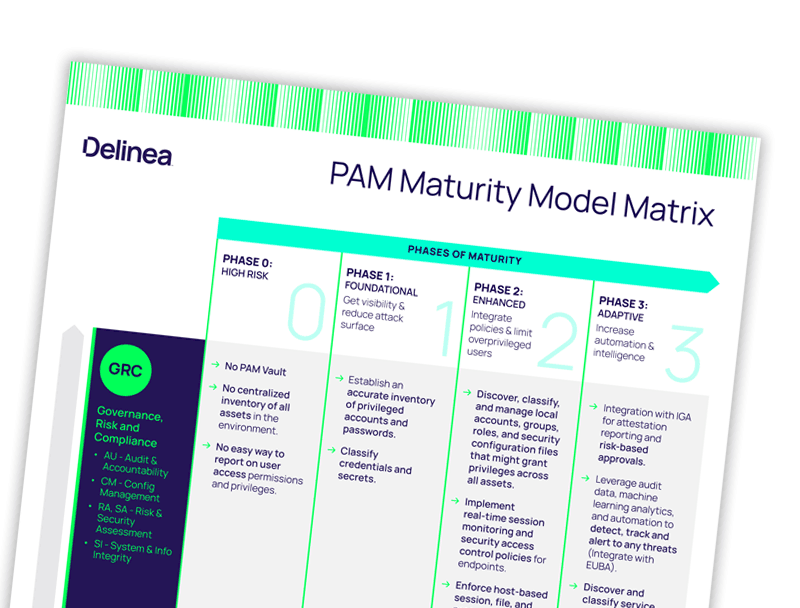
Each phase of the PAM maturity model helps you evaluate your level of maturity according to three factors:Governance, Risk, and Compliance (GRC) – How strong is the integrity of your system, and how much visibility and oversight do you have?
Privileged Administration – How do you create, define, and manage privileges across your organization?
Identity and Access Management – How strong are your authorization controls and how granular are your access controls?

See the quick guide to PAM maturity
At a glance, assess your level of maturity and see the PAM controls recommended for each phase and dimension.
Build a PAM maturity plan that’s right for you
Learn more about the PAM Maturity Model, including detailed descriptions of each phase and recommendations for increasing PAM scope and adoption to reduce your risk.

Evolving from PAM to Extended PAM

Introducing the New Delinea Platform

Model for Privileged Access Management Maturity
PAM solutions for every phase of maturity
Full-featured, free trials get you up and running fast
Secret Server
Discover privileged accounts, vault credentials, ensure password complexity, delegate access, and manage sessions.
Server PAM
Centrally manage identities and policies while enforcing least privilege for on-premise and cloud-hosted servers.
Privilege Manager
Remove local admin rights and implement policy-based application control in a single solution.
Account Lifecycle Manager
Seamless service account governance from discovery and provisioning through decommissioning.
DevOps Secrets Vault
Protect secrets DevOps teams and RPA tools need
