HOW STRONG IS THIS PASSWORD?
This tool is for educational purposes only. Recommendations made by this tool to improve password strength are generally safe but not infallible.
Any password submitted here is not stored or transmitted.
Need a stronger password?
How Delinea protects companies from cyber attack
Consider how many passwords exist in your workplace.
How many are as weak as the password you just checked?
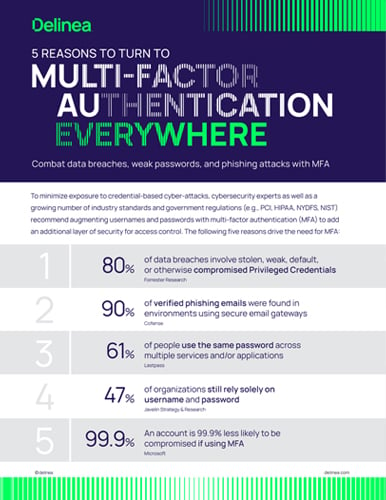
Employees have passwords to log into computers and online tools. IT admins have passwords that give them special privileges. Plus, enterprise systems like databases and applications have passwords to run programs and share information. If a hacker nabs a password – known to IT teams as “privileged credentials” – they can put your entire organization at risk.
80% of data breaches companies experience are related to privileged credentials that aren’t properly managed. Getting control of this issue has become the Security Officer’s #1 priority.