New research on future-proofing your cybersecurity strategy
Automation and expertise prepare enterprises for an uncertain future
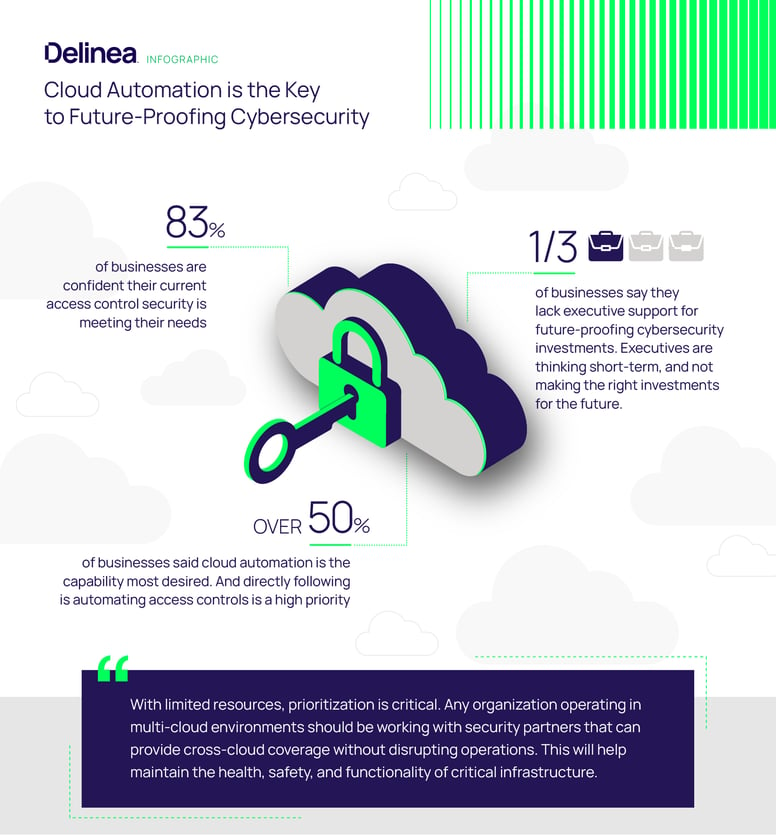
This research explores the important — yet sometimes misunderstood and undervalued — topic of “future-proofing.” We wanted to know how enterprises are preparing for an uncertain future by making investments that give them flexibility to meet changing security and business conditions.
We analyzed responses of more than 300 IT business decision makers, through a survey conducted in February 2022 by Censuswide, a global research company. The results point towards a balance of cyber expertise and automation, along with a healthy dose of reality to combat the risk of overconfidence as cyberthreats continue to rise.
The resulting report can help you build a cybersecurity strategy that supports your future growth while minimizing the shock and stress of rapidly changing technology and business conditions.
Get your copy to learn:
- Top challenges driving decisions, such as ransomware and hybrid-cloud environments
- Why increasing budgets still aren’t sufficient to solve security challenges
- Where decision-makers are investing to prepare their enterprises for the future
- Insights and recommendations from cybersecurity experts to guide your choices
Key Stats from the Report