PRIVILEGED ACCESS MANAGEMENT SOFTWARE FOR DEVOPS
DevOps Secrets Vault
Manage credentials for applications, databases, CI/CD tools, and services without causing friction in the development process
DevOps Secrets Vault provides instant availability of secrets, SSH keys, certificates, API keys, and tokens
Applications and databases
Enable app-to-app communications and app-to-database access without hardcoding credentials.
DevOps toolchains
Secure access to tools for software and infrastructure deployment, testing, orchestration, and configuration.
Robotic Process Automation
Centrally manage, control, and audit secrets for automated processes that operate without human oversight.
Reduce DevOps secrets sprawl across your attack surface.
With DevOps Secrets Vault you can securely provide secrets at the speed and agility DevOps needs to stay competitive
DevOps Secrets Vault helps you…
Establish secure vault
Manage secrets
Consolidate disparate DevOps vaults for easier secret rotation and a central audit trail.
Automate and scale
Match the pace of DevOps pipelines and RPA deployments with CLI and APIs.
Issue certificates
Issue X.509 and SSH certificates. Enable automated certificate signing and distribution.
Remove standing access
Provide Just-in-Time access to databases and cloud platforms with URLs that expire automatically.
Try DevOps Secrets Vault for free
See how you can simplify password management at DevOps speed and scale. Empower developers, engineers, and other IT teams to conduct their work securely, with a centralized, policy-based DevOps secrets management system.
Features |
|
|
Deployment |
Deploy rapidly with cloud-native SaaS architecture and elastic scalability that static, IP-based PAM solutions can’t provide. |
|
Advanced Automation |
Tap into command-line interface (CLI) and REST API. Simplify human navigation with CLI wizards for PKI, SIEM, Policy, and Auth-provider commands. |
|
Infinite Scalability |
Eliminate the need to add servers. |
|
High Availability |
Ensure 99.999% availability. |
|
Disaster Recovery |
Add a layer of protection with hot standby for rapid switchover. |
|
Local Caching |
Easily handle high-performance workloads. |
|
Cloud Authentication |
Assign AWS roles, Azure Service Principles, or GCP service accounts to servers (EC2, VMs) and authenticate to DSV. |
Download the DevOps Secrets Vault datasheet for more information.
Try DevOps Secrets Vault
free tool
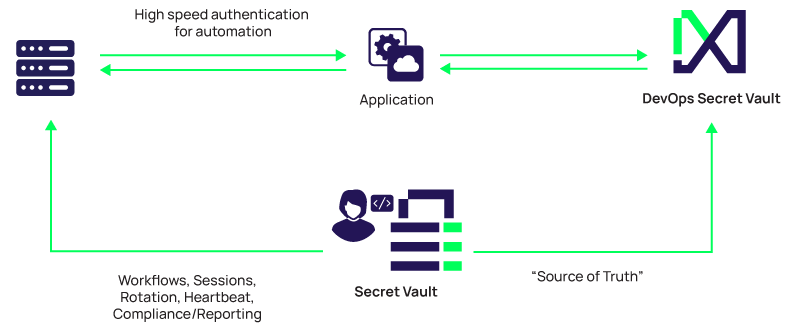
DevOps Secrets Vault supports extended PAM
The standard definition of PAM isn’t sufficient for the growing risk of cyberattacks. We believe PAM must address the exploding number of identities and today’s IT complexities.
Our products provide effective authorization controls for an identity-centric approach to security.
DevOps Secrets Vault
is optimized for machines
- Application to application communications
- Application to database access
- DevOps tools for software and infrastructure deployment, testing, orchestration, and configuration
- Robotic Process Automation
Secret Server is optimized for humans
- GUI centric
- Sharing Secrets/Controlled Access
- Session Management and Recording
- Heartbeat
- Password Rotation/li>
- Compliance and Reporting

Critical Controls for Modern Cloud Security
The rapid, iterative DevOps workflow exposes numerous security vulnerabilities.
Download the whitepaper to see how PAM for the cloud lowers your risk.
