Privileged Account Management (PAM)
What is Privileged Account Management?
Privileged Account Management (PAM) is the process of using software to control who gets the “keys to the kingdom.” Who can use a privileged account and access a sensitive server, adjust permissions, make backdoor accounts, or change or delete critical data? In other words, who can unlock a door to your network, enter, and affect what’s inside?
Privileged accounts exist throughout your organization. They provide teams with the building blocks for managing the hardware and software that power our information-driven, internet-connected world. Yet, for most users, privileged accounts are invisible.
Privileged Account Management is a top priority for most organizations. It serves as one of the most critical solutions to help organizations reduce the risks from cyberattacks that target their privileged accounts. Once compromised, a privileged account enables attackers to roam throughout a network undetected, downloading malicious payloads, staging compromised servers, and causing significant financial loss or damaged reputation among their victims.
What is a privileged account?
The typical user account is associated with a human identity such as an Active Directory user account and has a password that is meant to restrict access to the user account. Privileged accounts give administrative access based on escalated levels of permissions.
A privileged account can be human or non-human, and therefore should not always be associated with a human being. An example of a non-human privileged account is an application account that runs services requiring specific permissions. With many more employees working remotely, a human user account can also have elevated or administrative privileges attached to it.

Privileged Access Management For Dummies
Many organizations assume that privileged accounts mean only a domain administrator account or any user member of a domain admin group. While the domain admin is an essential privileged account, many more exist throughout the organization, posing a significant risk of compromise. When an attacker gains access to a privileged account, it only takes them a few steps to elevate privileges and get the credentials of a domain admin.
Like user accounts, privileged accounts have passwords to control access. The problem is that cybercriminals have a variety of tools they can use to crack these passwords. After an attacker gets access to a password-protected system, the damage can be catastrophic. Getting access to and taking over privileged accounts gives attackers the ability to download an organization’s most sensitive data, distribute malware, bypass existing security controls, and erase audit trails to hide their activity.
How do you get started with managing privileged accounts?
Traditionally, organizations have relied on password manager software to help employees maintain and secure passwords. However, this approach relies on the employee choosing and managing those passwords appropriately.
Organizations today are moving beyond basic password security to manage privileged account passwords more efficiently by deploying robust privileged account and access management solutions. Thus, privileged account management tools help your organization improve password protection and strengthen privileged account security overall.
However, you cannot manage your privileged accounts if you don’t know how many you have or where they are. Start by using a privileged account discovery tool. A discovery tool will speed up your knowledge and understanding of how many privileged accounts you think you have versus how many you will discover with a thorough search and review. Knowing where your privileged accounts reside throughout your environment is only the first step. You should go further and conduct an audit to identify the location of all privileged accounts properly.
Next, follow the Privileged Access Management Lifecycle approach for an invaluable method for ensuring any PAM solution covers all your needs in safeguarding your privileged accounts. The entire process is shown in the diagram below and described in detail in the free eBook Privileged Account Management for Dummies.
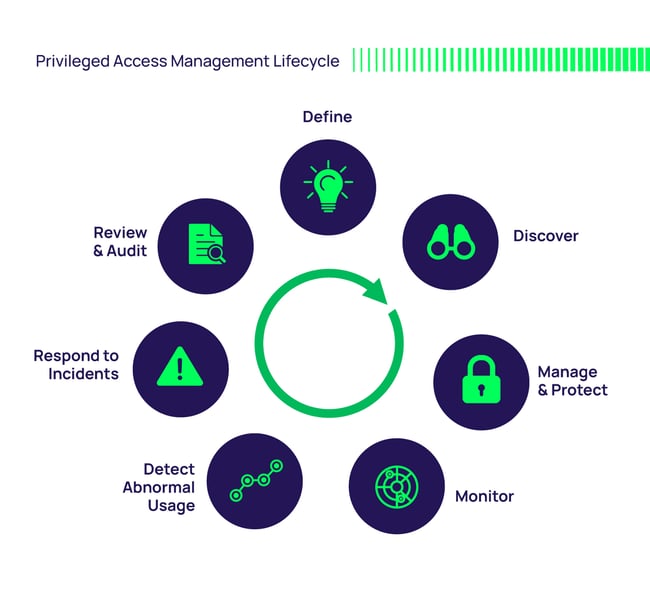 The steps in the PAM Lifecycle are detailed here:
The steps in the PAM Lifecycle are detailed here:
The Privileged Access Management Lifecycle and Path to Maturity
What’s the difference between Privileged Account Management and Privileged Access Management?
Over the past several years, the term Privileged Account Management has evolved and been encompassed in the label: Privileged Access Management. This is an acknowledgment that not only should privileged account passwords be safeguarded to properly verify the identity of the person or service accessing a privileged account, but what that person or service can do once verified must also be an essential component of any PAM solution.
More Privileged Account Management Resources:
Blogs
The 7 Deadly Privileged Accounts You MUST Discover, Manage and Secure
A Guide to Managing and Securing Privileged Users
eBooks
Privileged Access Management for Dummies
Free Tools
Free Privileged Account Discovery Tool for Windows
Free Privileged Account Discovery Tool for Unix
Whitepapers
How to Instantly See Privileged Account Compromise or Abuse
Products
Protect your Privileged Accounts with an Enterprise-grade PAM Solution
What does cybersecurity like this cost? Not as much as you think
