Research shows remote workers face tough choices between productivity and security

Joseph Carson
Delinea just completed a global cybersecurity survey among 8,000+ knowledge workers in 15 countries in partnership with Sapio Research. Survey results reveal a disturbing (if not surprising) disconnect between an understanding of cybersecurity risks in 2021 and the risky activities employees engage in every day to get their jobs done.
This new survey and report is a cybersecurity reality check, that reveals striking similarities and differences among countries around the world dealing with a pandemic that has thrust many more employees into remote working conditions.
Many employees believe they are not important enough to be targeted by attackers
You can get free access to the full report here. For now, I’ll highlight the major takeaways and provide recommendations that can help companies of any size throughout the world protect their remote workers from the latest cyber threats.
Here are the top survey takeaways:
Despite knowing the security dangers, 79% of employees still engage in risky behavior
Dig into the research and it becomes clear that far too many employees believe they are not important enough to worry about security risks and therefore not a target of attackers and cybercriminals. This perspective makes them more likely to engage in risky behaviors to get their jobs done.
Here are some examples:
More than a third of employees (35%) continue to save passwords within their internet browsers on all of their personal and work devices. By cracking only one of those devices, an attacker can easily access all the passwords stored within the user’s browser. This makes it so much easier for an attacker to elevate privileges without being detected and gain access to the user’s email, company cloud applications, or even sensitive data.
If the employee has saved multiple passwords within the internet browser, an attacker can readily see whether they are all the same or simple variations such as one character difference. Leveraging this information, an attacker can use password cracking tools and wordlists to create all possible combinations of an employee’s password choices. It’s then only a matter of time before the attacker can gain access to all of an employee’s accounts, including their company’s applications and systems.
Other alarming indicators from the survey show that more than half (55%) of the respondents believed it’s okay to connect to a mobile hotspot in a work-based scenario and one-third (34%) have sent a work document to a personal computer due to a work device malfunction.
A partial explanation for remote workers continuing to rely on risky behaviors may stem from a false sense of security. For example, even though 86% of employees expressed a personal sense of responsibility to ensure they are not exposing their organization to cyber threats, more than half (51%) of respondents say their IT department should be solely responsible for protecting them and their organization from cyber threats.
Thus, employees may be continuing to take risks based on the assumption that even if they do something wrong that leads to a security incident, their security team will take care of the problem for them.
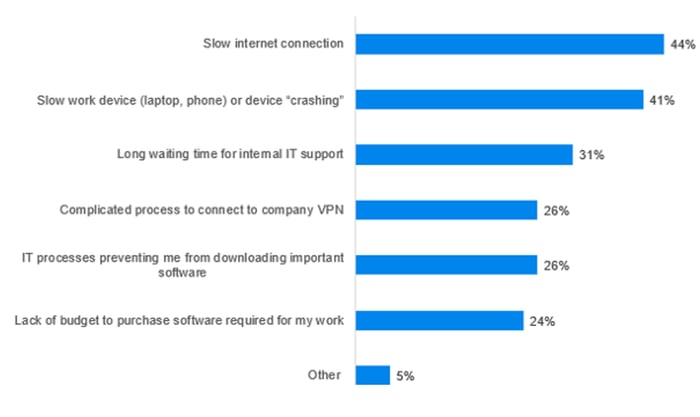
Remote workers face continuous frustration with internet connections and software issues
The survey report indicates that nearly half of all remote workers across the globe have struggled with basic issues such as slow internet connections and slow work devices during the past year. Obviously, the pandemic has accelerated a trend to remote working, but the infrastructure that supports it has failed to keep up in many cases. That means any impediment to getting work done puts a further strain on workers trying to maintain a balance between security and productivity.
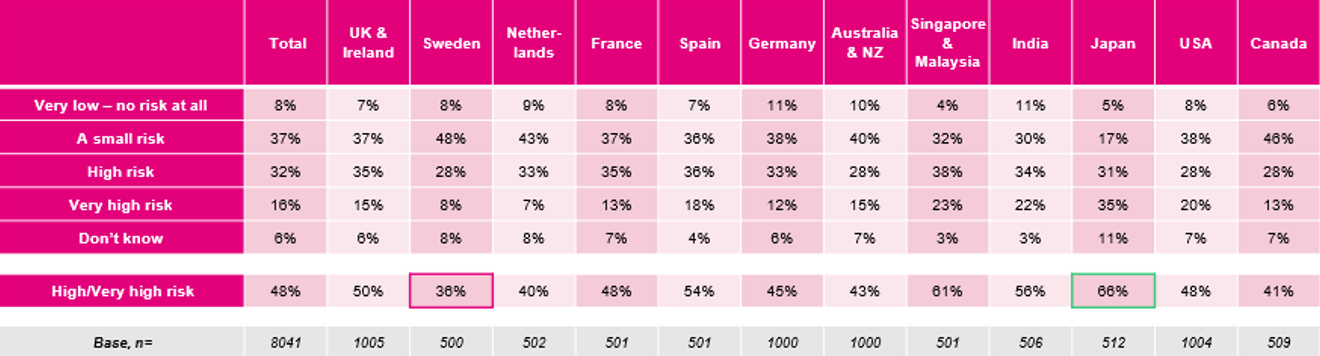
Employee perceptions of risk and behavior variations by country
When it comes to assessing risk from cyber attacks, the report reveals some interesting variations among the countries surveyed. More than one out of three Swedish knowledge workers, for example, are less likely to perceive a high or very high risk (36%) from cyber attacks.
In contrast, two-thirds of Japanese knowledge workers (66%) are likely to perceive the risk from a cyber attack as high to very high risk. Japanese knowledge workers are also the least likely to have engaged in risky business, such as clicking on unknown links or using repeated passwords, while those in India are the most likely to have done so.
This is only a sampling of the survey results—download the full research report here.
How do we protect users given such varied perceptions and risky behaviors?
How do IT security teams deal with such wide variations in risk perception and risky behaviors? Clearly, cybersecurity awareness and education must continue across the board to help all employees understand the risks involved in their everyday actions. And while training takes time and results are not always consistent, cybersecurity professionals can gain some control immediately by making use of automated technology—“behind the scenes” if you will.
The survey and report tell us that cybersecurity teams must build secure behaviors in the workplace wherever possible. Too many organizations are still protected with just a simple password, with employees given the responsibility for creating and managing their own password complexities on a continuous basis. As the research shows, that approach falls far short in a world dominated by ever more sophisticated cyber threats and productivity demands on users.
Cybersecurity teams should move password and privileged access security into the background so their employees do not need to create, rotate, or manage them. This will go a long way to enabling employees to focus on the things that really matter, like staying productive, meeting their business goals, and being successful in their organizations.
Your cybersecurity tools must be easy to install, deploy, and manage
Usable cybersecurity tools must be easy to install, deploy, and manage for business users as well as IT managers. Tools or techniques that interfere with employee productivity are doomed to fail. User experience has to be a top priority for all security measures.
At Delinea we have refined the concept of “Invisible PAM”—PAM that focuses on delivering Privileged Access Management by balancing security and productivity behind the scenes. Too many traditional PAM solutions require people to interrupt their workflow to securely access the credentials they need to get the job done. As a result, they find ways to skirt security policies so they can stay productive. A PAM investment that’s supposed to protect them can sit on the shelf collecting dust or be simply bypassed with a workaround.
For the average privileged user, PAM should be virtually invisible
Delinea believes PAM complexity isn’t just a hindrance, it can also be downright dangerous for the user and the entire organization. Usability and security must go hand in hand to increase adoption and decrease risk. To realize the benefits of enterprise PAM, solutions must be easy to use, embedded in people’s daily workflow, and orchestrated behind the scenes. For the average privileged user, PAM should be virtually invisible.
Learn more about the advantages of “Invisible PAM” in this whitepaper.

FREE TOOL
Cybersecurity Incident Response Template