Privilege elevation for workstations and servers

Sara Shuman
“Start with the end in mind.”
That’s how people tell you to face a challenge. While that’s true, the end can sometimes look so far away you feel overwhelmed before you even begin. When that happens, the best thing to do is set small, attainable goals along the way.
You can use the same strategy on your Privileged Access Management (PAM) journey. If you’re in the beginning stages of PAM maturity—and that’s most companies—the idea of reaching the more advanced stages can be daunting.
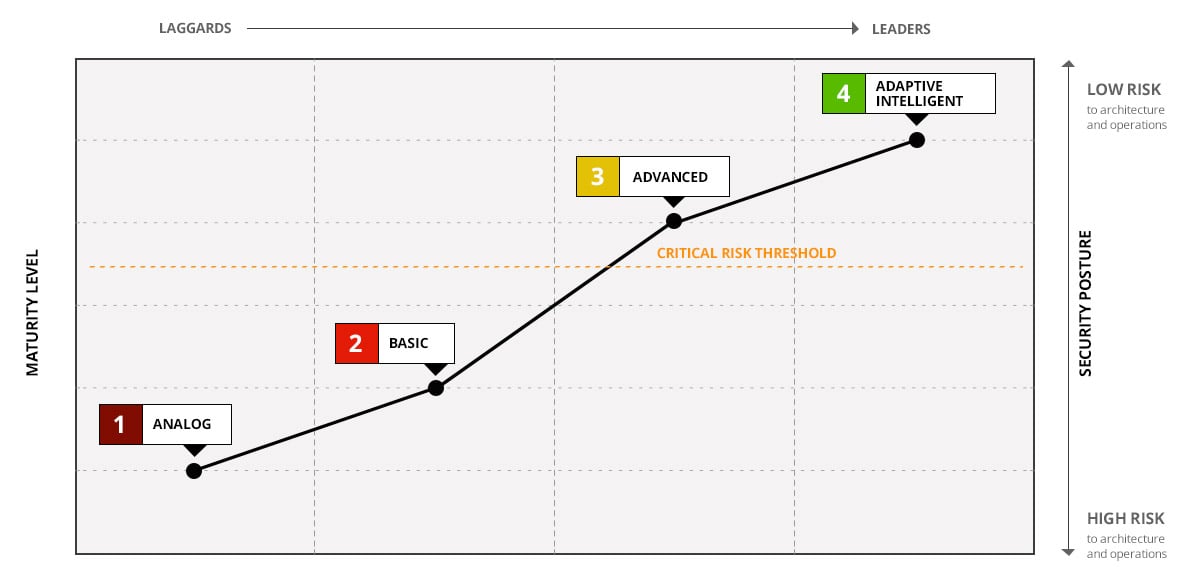
The good news is that you don’t need to take on everything at once. In fact, we suggest you don’t.
We find that most organizations start strong when they adopt PAM. They get the vault set up and get domain passwords and local shared accounts under control. Then, they start to get complacent. They stagnate on their journey somewhere between stages two and three.
Most organizations start strong then stagnate somewhere between stages two and three
Meanwhile, the organization keeps growing and the IT environment gets more complex and difficult to manage Service accounts proliferate, unchecked. Identities multiply and become siloed in Active Directory, LDAP, etc. This is especially true for Linux systems in the cloud; with no centralized management like AD, local accounts abound. Cloud platforms like AWS have their own IAM services, which leads to more siloed accounts.
Just as technology mushrooms, the number of privileged users grows exponentially. Business users adopt more applications without IT management. Engineering teams spin up more systems, and developers store passwords in libraries and code.
Meanwhile, cybercriminals are getting more sophisticated and emboldened all the time.
To protect your growing attack surface, you can’t stagnate at the Basic stage. The jump to Advanced is an important one, and it’s manageable. Let’s break it down.
Fundamentally, the Advanced stage of PAM maturity is about implementing a zero trust model founded on the Principle of Least Privilege (PoLP). With this approach, users and systems should have only the accesses and permissions they need to do their jobs, nothing more.
Traditional password vaults offer a basic level of control and fundamental security benefits. Password theft, however, is only one step in a cybercriminal’s attack chain. Should an attacker successfully gain access to a system, they will also need the ability to export data without detection, so they can sell it on the black market or ransom it off. To further secure your organization, and mature in your PAM program, privilege elevation solutions should be used. This will allow you to assign admin rights to individual tasks, applications, or scripts that require them for a granular level of control.
There are two parts of your attack surface where maintaining least privilege is essential for a strong security posture: user workstations and servers. In both situations, privilege elevation capabilities allow you to easily assign or revoke privileges for a specific period, providing just-in-time, just-enough access when admin control is absolutely necessary.
User workstations and privilege elevation
More than 80% of cyber attacks begin at the endpoint. User workstations often contain local administrative rights, and, because they’re often used remotely, on less protected networks—such as Starbucks or the airport public WiFi —they’re easier to hack than servers.
Most IT organizations simply allow the workstation user to routinely log in with a local admin account. Thus, if that user is phished, the bad actor immediately inherits those administrative rights and owns the system. What’s more, a cybercriminal can leverage those local admin rights to progress to other systems throughout the organization.
Removing administrative rights from user workstations is a crucial step in your PAM journey. In fact, 60% of all Microsoft vulnerabilities published could be mitigated by removing admin rights from workstations.
Delinea Privilege Manager helps you discover and remove admin rights from Windows, Mac, and Unix/Linux workstations. It can also automatically enforce your least privilege policy without impacting user productivity with seamless application control. When users require additional access rights to run specific applications or make changes to their workstation, application control temporarily elevates their privileges for a particular purpose.
Servers and privilege elevation
One main benefit to implementing least privilege is limiting lateral movement across the network. This is typically the way attackers access sensitive data. Just as nobody should have a single key/badge that accesses everything in your organization, routine use of superuser accounts (e.g., root and administrator) on a server should not be allowed. Additionally, since these superuser accounts are unfortunately often shared, there’s no accountability, no easy tie back to the real user, making incident investigation and compliance auditing more challenging, if not impossible.
If we follow the best practice of eliminating standing privileges by removing these shared privileged accounts, we can stop lateral movement, ensure accountability, and reduce risk. Delinea's Privilege Elevation and Delegation Management (PEDM) solution governs and controls access and privilege for Windows, Unix, and Linux, providing highly granular, role-based access controls that simplify implementing a least privilege model.
Roles and policies for cross-platform access and privilege are centrally managed from Active Directory. Administrators can systematically request a new role to obtain the rights they need to perform tasks, using native workflow or integrated systems like ServiceNow and SailPoint.
You can also isolate servers based on time and trust relationships to further protect sensitive data.
Fine-grained auditing and visual session recording occur on each host and can’t be bypassed. This structure guarantees complete visibility of privileged activity and a forensic level of detail to support incident response and compliance activities.
Take the next step in your PAM journey
The truth is, there isn’t an “end” to your PAM journey. Reducing cyber risk is an ongoing pursuit.
You can accelerate along the PAM maturity curve by shifting your focus from PAM as a password vault to a broader view of PAM for the just-in-time, just-enough privilege. Let’s talk about how you can make the jump from basic maturity to advanced.
Implementing Least Privilege shouldn't be hard


