Beyond Password Managers

Barbara Hoffman
Passwords should be complex. Password management should be easy.
Consumer password managers are popular solutions for personal password storage. These digital password vaults make it possible for you to have different, complex passwords for each website and application you use. Password managers also help you avoid bad habits like using the same password for multiple systems or writing them down and storing them in places where they are not secure, like stuck to your monitor or under your mousepad.
How do password managers work?
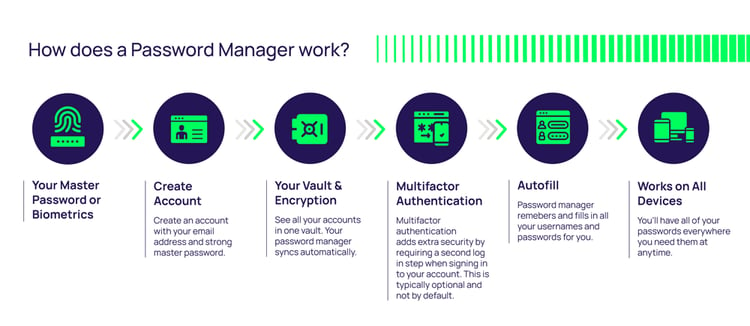
A password manager is a small vault (typically a database) that stores all your credentials and passwords—encrypted— and is usually protected by a master password or by biometrics, sometimes with additional authentication protection such as two-step or multifactor authentication (MFA). In most configurations, unfortunately, the additional authentication protection is disabled by default and must be enabled by the user.
You can usually create multiple vaults, each protected with a master password. The most common way to create new entries in the vault is via a browser extension. Then, when you’re entering information into a username and password field on a web form, the extension will offer to save those credentials in the vault. The fields can then be automatically populated the next time you go to the same website.
The vault can be synchronized across multiple devices providing you with an effortless way to fill out your username and password on web forms without having to remember your password or type it in directly. A password manager helps you generate strong passwords for each account and audit the strength of your unique passwords.
Some versions of password managers allow sharing of credentials with family members.
This diagram represents how password managers work:
What makes personal password managers appealing to consumers is that many basic password manager applications offer free versions, albeit with limited features. Once you hit your password limit or you want more functionality, such as the ability to sync across multiple devices, payment is required, and the more features you need the higher the price
Password managers do have their strengths.
With password managers, passwords are encrypted and can only be decrypted when accessed in conjunction with a user-generated master password. Most password managers store the credentials used to access multiple accounts and applications: username, password, application name, website URL, or IP address of the system. They can be installed locally, accessed in the cloud, or via mobile apps. And they’re designed to generate long complex passwords and auto-populate the password into the correct field, so people don’t have to manually key it in or cut and paste.
Are password managers better than creating your own passwords, and writing them down?
For an individual who wants to protect personal passwords, using a password manager might be OK. It’s certainly better than passwords written on post-it notes stuck to a monitor or taped under a keyboard, saved in Excel spreadsheets or Google docs, or stored in plain text using a browser plugin.
But does it make sense to use one of these personal password managers to secure corporate passwords?
If your goals are enterprise security and efficiency, password managers are not enough. For companies, a Privileged Access Management (PAM) solution is preferable, and for reasons that extend far beyond security alone.
Benefits of PAM over personal password managers
A unified approach to corporate password management with enterprise-level PAM is more secure and efficient than thousands of disconnected personal password managers.
Privileged Access Management is a more robust security solution than password managers. Look for a PAM solution that offers the following features:
-
High availability
-
Compliance and regulatory security controls
-
Automated privileged account discovery
-
The ability to configure access approval workflows
-
Integrations with enterprise solutions like ITSM, IGA (Identity Governance and Administration), and SIEM (Security Information and Event Management)
-
Ability to scale across the business
-
Automated password rotation
-
Auditing and reporting on password usage and security
-
Consistent security controls
Organizations use PAM software to control who can use a privileged account or access sensitive information with the ability to adjust permissions and change or delete critical data. They treat the privileged account as the object that is being protected, restricting password disclosure and sharing, all while providing time-limited access to critical systems. Once a password is no longer required it’s rotated or expired so employees and third parties can’t continue to access sensitive information with old
Individual responsibility vs. corporate responsibility
Password managers require that individual users set up, maintain, and always use the app. The user assumes all responsibility for keeping the technology up to date and functioning properly.
With LastPass, KeePass, Dashlane, and other personal password managers, the user is accountable and responsible for password security. They must do the heavy lifting of setting up, password rotation, and, most importantly, making sure the password vault is used all the time.
With an enterprise PAM solution, the IT team assumes responsibility for the tech behind corporate password security. They do the work of getting it started and keeping it going. All the user does is enjoy it.
Integrating password management into users’ daily workflow
Many business users don’t consider password hygiene a top priority, less so if it interferes with their productivity. They are more likely to adopt secure password practices that are integrated into the workflow and systems they use every day.
Personal password managers aren’t integrated into enterprise tools. They require a user to stop doing what they’re doing, open a separate tool, and then go back to their first screen to continue their work.
Privileged Access Management solutions, on the other hand, are integrated directly into a user’s workflow. In fact, many users never ever need to see the interface of an enterprise PAM solution like Delinea’s Secret Server, because the system acts behind the scenes.
PAM solutions automatically create and rotate passwords, ensuring that when passwords are changed, all dependencies—systems that are connected to those passwords—can still authenticate and connect. With PAM, you can design sophisticated rules about what should happen after a password has changed. Session launchers within PAM tools make it possible to give people access to your IT systems, even temporarily, without requiring them to insert or even see a company password. This functionality is particularly helpful for organizations that engage with contractors and third parties.
Non-human privileged account management
Personal password managers work best with human-to-application credentials, but they fall flat with application-to-application and other non-human credentials. Once you need to protect devices, data, code, and applications in the cloud, a password management system simply can’t keep up.
Organizations can adhere to consistent policies with a single solution for all types of privileged accounts
Enterprise PAM solutions manage more than privileged user accounts. They also manage service, application, database, and other non-human accounts. PAM protects all types of secrets, keys, APIs, and other credentials that control access to IT infrastructure, and provides fine-grained authorization. With one solution for all types of privileged accounts, the entire organization and IT environment can adhere to consistent policies and practices.
Central visibility and oversight
Personal password managers don’t offer the visibility and control organizations need to protect sensitive data, meet regulatory requirements, and manage at scale. When every user manages their own passwords, it becomes extremely hard to track how and where passwords are being used and stored, and whether those passwords are sufficiently protected.
Enterprise PAM solutions continuously discover and manage all privileged accounts and associated passwords throughout your organization. They provide central oversight such as session management and monitoring for privileged account behavior.
Auditing and reporting
To satisfy auditors, you need to do more than secure company passwords. You must track the actions users perform while accessing privileged accounts, then report on that activity without spending hours combing through logs.
Consumer-grade password manager tools typically don’t include an immutable audit log, customizable reports, and session monitoring or recording.
Enterprise PAM solutions offer session recording capabilities to enable forensics and generate compliance reports that satisfy auditor requirements.
Are you researching password managers and enterprise PAM?
Secret Server Free is Delinea's free Privileged Password Management tool for IT Teams and an easy step into enterprise password management.

FREE EBOOK
Privileged Access Management For Dummies



