IAM: The future of identities and how we’ll get there

Joseph Carson
Identity and Access Management (IAM) is the ability to provision, manage, audit, and secure digital identities to facilitate and enable approved, authentic requests or connections to view company data, services, systems, networks, and assets. This applies whether they are located on-premise or in the cloud, based on roles and privileges assigned to each digital identity, both human and machine.
Digital identities are the foundation of a digital society. It is important to first understand some of the terminologies that are related to building digital identity and digital trust.
Identity Terminology
Access Management – the process of managing user access to resources
Authentication – The process of verifying a digital identity
Authorization – The process of verifying a digital identity should have access to a service or resource
Attributes – information associated with the digital identity such as name, address, location, or number
Credentials – information that pertains to the integrity of identity attributes such as a username or password also known as a Secret
Data Brokers – the entity responsible for managing access to data
Identification – The process of determining which attributes are gathered and verified for accuracy
Identity Proofing – the process of uniquely identifying the user, validating authenticity, checking the accuracy, and verification of the claim at the time of authentication
Level of Assurance – the confidence level that the identity is authentic such as the security controls satisfied during authentication
Level of Trust – the process of determining business risk exposure and whether more security control must be satisfied
Privilege – the level of access authorization that allows access and entitlement for a group or user
Growth of Digital Identities
Digital identities have been growing in popularity and implementation over the past few years, especially within national governments. Some countries that have implemented digital identities include Belgium, Cameroon, Canada, Ecuador, Estonia, France, Jordan, Kyrgyzstan, Italy, Iran, Japan, Senegal, and Thailand. In the near future, we’ll see digital identity enabled across multiple industries and governments that will be used for voting, tax returns, banking, passports, unlocking doors, starting vehicles, public transportation, or access to health services.
A problem in the past was that many citizens saw government-issued digital identities as a way to control citizens or a mechanism to spy on all citizens’ daily activities. A government-issued digital identity or a digital identity that can be provisioned for government services will enable governments to evolve into digital government service providers. A successful program will rely heavily on both transparency and trust.
Ultimately, the citizen is the owner of the data, and non-repudiation of usage and access of the data is critical to providing and building digital trust. But for governments to provide better digital services they needed a way to deduplicate data across multiple government agencies’ data repositories.
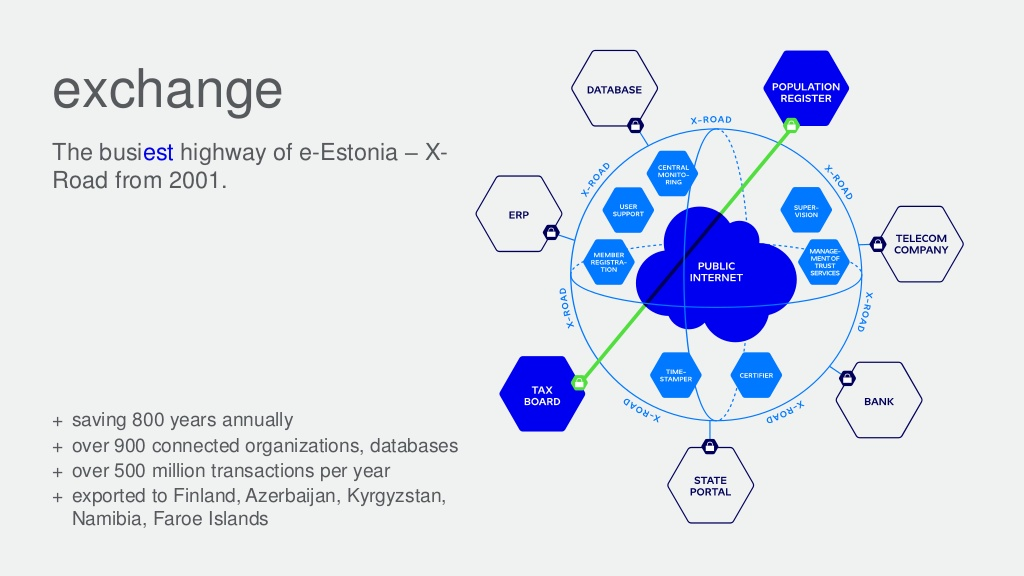
Once digital identities are in place, then there’s an opportunity for citizens to BYOI (Bring Your Own Identity) and companies will be responsible for provisioning, authentication, and authorization. For example, in Estonia, all citizens have a government-issued identity that can be used to log on to work systems, access healthcare resources, conduct banking, vote, park their car, or even use loyalty cards for shops. Estonia definitely has innovated its digital identity system. Other nation-states and companies are not far behind, but their implementations will be somewhat different and based on a variety of technologies and use cases.
View more information on the Estonian Digital Society.
A big element of digital identity is trust and the root of trust. This is determined by the continuous trust of the Identity Provider and the accuracy of the attributes provided. Think about when you meet someone for the very first time and you really don’t know the person. They provide you with some identity attributes, but at this time the level of assurance is low. You then identify a mutual friend who knows both of you and you can verify with your trusted friend that the attributes provided by the new person are accurate and valid. You can then establish a new level of trust but not higher than the root of trust.
So outside of digital identities, what other shifts can we expect around identities and IAM?
Convergence of IAM and Privileged Access Management
We’ve already seen IAM and Privileged Access Management (PAM) converge to secure and protect privileged access to systems and data. Now dynamic security will increase or decrease the security measures depending on a global risk score or threat level to the organization or industry and federating entitlement and compliance. For example, if a new major data breach occurs that puts many organizations’ identities and credentials at risk, the combination of IAM and PAM can increase the security controls required and rotate existing passwords of suspected high-risk credentials.
Security must be like a living organism that can adapt to global risks and increase or decrease security as the threat landscape changes. The level of security, of course, can impact friction with employees, so it is important that during normal operations the security controls have zero friction and visibility for employees. This ensures usable security and increases the effectiveness of controls.
IAM and Trust-Based on Behavior and Reputation
IAM will use behavior and reputation mechanisms that will establish an identity footprint and will challenge the identity when the digital footprint differs significantly, such as locations, browsers, patterns, and paths. For example, when employees are accessing from countries where your organization doesn’t have offices, then you might require additional levels of security controls to be satisfied or even require access workflows, where an employee peer must approve the access while the employee is in that location.
Another example is an employee who uses a different device to access the company cloud applications but has valid credentials. However, there is increased risk so the security controls might limit the employee to having least privilege on the cloud application because the endpoint is not managed, thereby reducing the possibility of data loss or access abuse.
IAM for IoT
IAM will be used to enable effective and secure IoT. When you purchase your next vehicle, you will not get a key, but your digital identity will be provisioned to use and access the vehicle, and IAM will make that possible. The same will be true when renting a scooter or using public transportation, which will all be linked to your digital identity. Your digital identity could also be used for unlocking both your home and office doors, communicating with home automation, such as robot vacuums, heating or lighting, or even shopping. In Estonia today, you can also use your government digital identity to get drinks from vending machines. IoT devices need access and to enable secure access they need to integrate with digital identities.
Watch the following video to learn more about IoT Security:
Risk-based Authentication
Risk-based authentication solutions will use calculative measurements to determine if it is safe to continue. A risk-based approach will check any number of items:
- Where I am accessing from?
- What is my level of privilege?
- Does my system meet compliance?
- Do I have a VPN connection open?
- Is the channel encrypted?
- When was the last time my digital identity was used for the same request, reputation on other systems?
- Do I have any open incidents?
If the network from which I am accessing is privileged, then the risk of allowing my authentication is higher, and therefore I should be challenged for an additional factor(s) of authentication. A risk-based approach will use dynamic security measures depending on the risk. If the risk is too high, then the request is denied. A dynamic approach automatically increases the security parameters when the threat level is high and decreases them when the threat level is low.
Identity Management and Governance (IMG)
IMG will enable perimeter-less and borderless access. Today the perimeter has almost evaporated due to cloud, mobility, and connectivity. Digital transformation has accelerated, and IMG will enable companies to serve their employees, customers, and businesses without the need to have a perimeter around the network. Already, virtually all devices are internet-connected and the challenge is to ensure security on each device through strict privilege account management.
Identity as a Service (IDaaS)
IDaaS is simply the ability to use cloud resources to provision digital identities, single sign-on, and federated access management. IDaaS will expand to hybrid models where on-premise accounts will be via an on-premise identity management solution and cloud accounts via a cloud or IDaaS solution. This means that employees can access cloud solutions provided by their employers without the need to authenticate via the organization’s internal network. This also allows a company to enable third-party access without the need to ever provision an on-premise account in Active Directory. IDaaS will enable business-to-business identity federation capabilities so as not to provision accounts on internal systems.
Deception technologies are basically modern-day active honeypots that will be used with IDaaS to help lure in attackers with fake identities and discover the attack paths and the hacking techniques they use in an attempt to gain access to the company’s network and systems. This will help organizations learn more about how attackers behave when attempting to laterally move once they’ve breached a system and identify the best techniques to reduce the risks from cybercriminals.
Blockchain and Identities
Blockchain will be key to IDaaS to validate and verify the integrity of systems. Blockchain is mostly known today for digital cryptocurrencies; however, blockchain has been used for many years prior to verifying the integrity of data and chain of custody. Blockchain will be used to deliver continuous non-repudiation of digital identities and the chain of trust. It helps prevent modifications or changes in historical events.
In Estonia, blockchain is used to prevent tampering of the digital identity and digital signatures used in the digital society ultimately removing the government as the root of trust so even the government cannot change the history of events. One way they ensure the integrity is by printing the root hash periodically in the Financial Times, helping to keep the integrity of the Estonian Digital History. Blockchain technologies in IAM will be delivered from the cloud as a service and in hybrid models.
Want to learn more from Joseph Carson—Delinea’s Chief Security Scientist—about the Nation-States Cyber Security, Digital Society, Cyberwar, and Blockchain? Register for free and watch the following session:
UK 2018: Blockchain in Security. Lessons Learned from Nation State Experience
How We’ll Get There
Digital identities are coming fast and a variety of different implementations are already taking place around the world. But it’s clear that IAM with strong Privileged Access Management is fundamental to creating digital success.

FREE WHITEPAPER
Take your Privileged Access Management to the Next Level