Global Benchmark Report: Companies have a long way to go to protect privileged identities and access

Joseph Carson
Privileged Identities remain the most sought-after attack vector for cybercriminals. Threat actors are increasingly searching for weak entry points they can exploit to access private systems and applications. Unfortunately, many businesses lack the proper identity verification mechanisms and strategies needed to thwart incoming attacks—making them highly vulnerable to cyber threats.
Our latest IT security research, which surveys 2,100 security and IT decision-makers around the world, sheds light on how organizations are approaching Privileged Access Management (PAM) as a strategy for reducing identity-based attacks. The report—Global Survey of Cybersecurity Leaders: Benchmarking Security Gaps & Privileged Access—also explores some of the key obstacles, security gaps organizations face, and the progress they’re making in cybersecurity today.
Interesting takeaways from the report
Based on our findings, it’s clear that security teams are prioritizing identity security, which is no doubt great news. However, there are still obstacles that companies need to overcome to properly secure their digital assets. Many businesses are now in a race against time as they work to upgrade their defenses before experiencing a devastating cyberattack.
With this in mind, let’s examine three high-level takeaways and benchmarks from the report.
1. Companies are behind the curve with PAM
On one hand, 90% of respondents agree that identity security is important for meeting business goals. What’s more, 87% agree that securing identities is a top priority for the next 12 months.
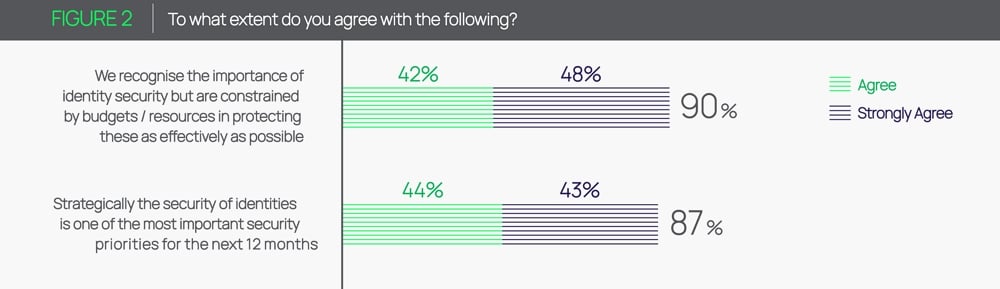
Despite this, many businesses are far from where they want to be in their overall security readiness. As it turns out, 60% of companies say have a long way to go to protect access and privileged identities like administrator and root accounts.
In terms of benchmarking differences among companies, the research reveals a growing gap between regions that have PAM best practices and those that lack them. For example, organizations in Africa and the Middle East are especially at risk for privilege-based cyber attacks.
2. Machine identities are vulnerable to attacks
The report also reveals that user identities are currently receiving the lion’s share of attention from security professionals. Businesses are failing to properly protect machine identities that authenticate and establish trust with other systems and resources. More specifically, only 44% of machine identities and 42% of privileged identities have privileged access security measures in place.
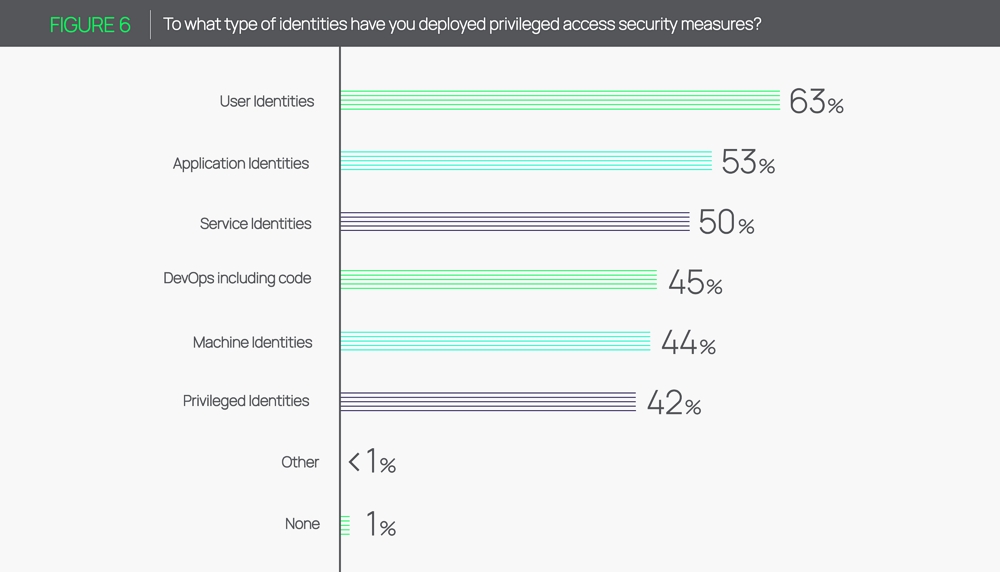
This is a big deal when considering that organizations typically have large attack surfaces, with hundreds or thousands of privileged accounts. However, businesses only manage and secure a small amount of them. And as a result, many remain vulnerable to attacks.
3. Businesses lack identity management support
Most organizations are making plans to invest in additional security measures and enhancements. Our report found that 39% of companies say their top priority in the next year is adding more security controls to protect privileges.
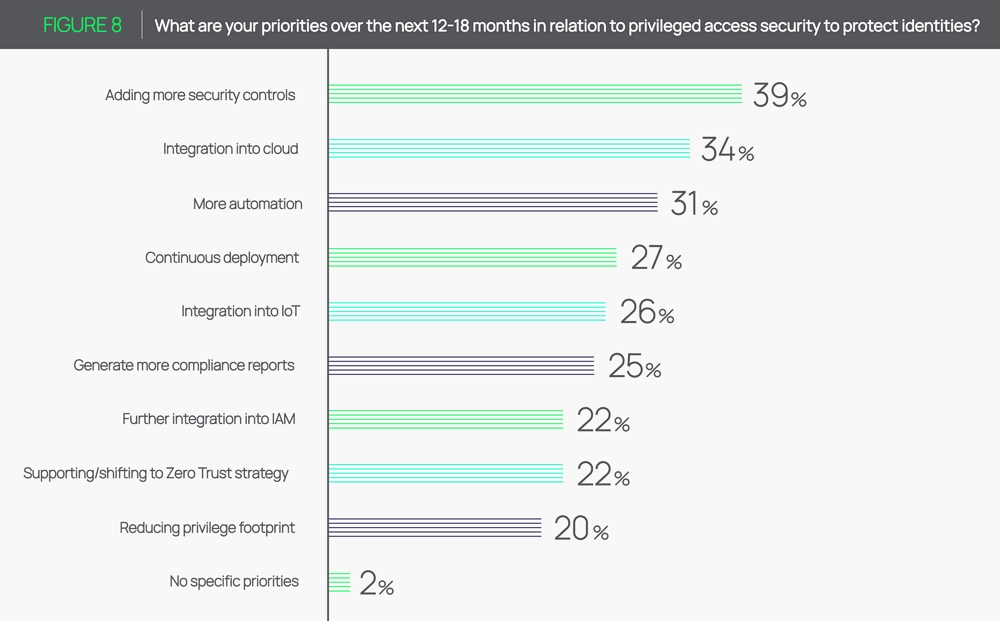
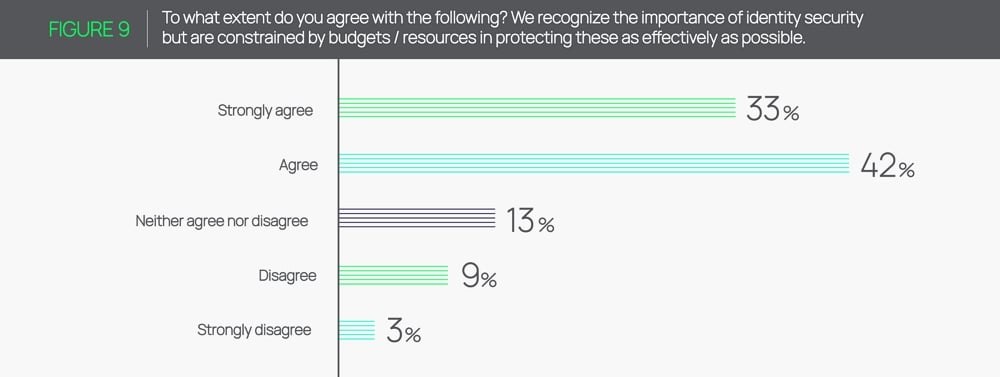
What’s less encouraging is that 75% of companies believe they will fall short of protecting privileged identities because they lack adequate support due to budgetary constraints.
Equally alarming, only 37% of respondents say their company’s board understands identity security and views it as an enabler for better business operations. This suggests that security leaders need to do more to convince key decision-makers to make identity security a priority internally.
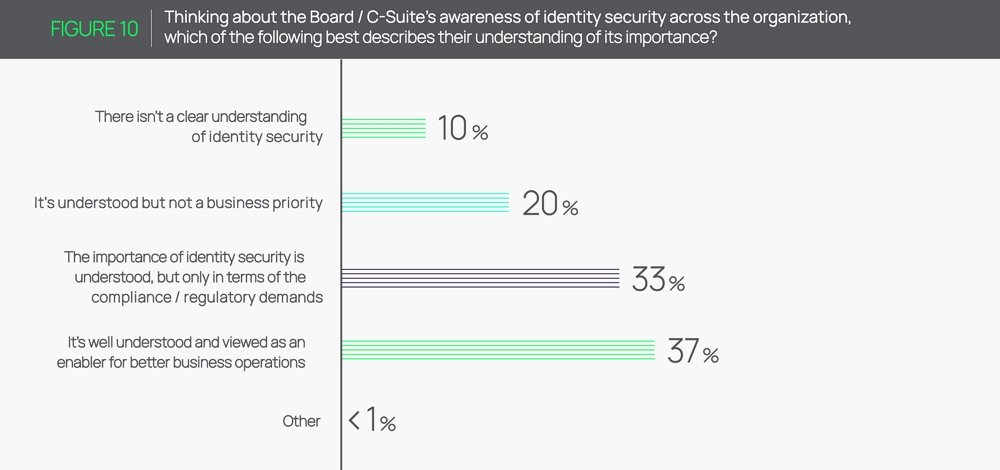
Furthermore, 33% of respondents say their board or C-suite understands the importance of identity security but only in terms of regulatory and compliance demands. In other words, many businesses are simply investing in identity security as a means of checking off compliance boxes and avoiding penalties—not to fortify their networks and systems.
Access the global report today for critical cybersecurity benchmarks!
Strong privileged access security isn’t something that you can build overnight. It requires communication and cooperation across all business levels—especially from key decision-makers with access to critical supporting resources.
If you’re looking to improve your organization’s cybersecurity stance, it helps to benchmark how other companies are approaching privileged identity and access management. For the full scoop, download the free report today:
Global Survey of Cybersecurity Leaders: Benchmarking Security Gaps & Privileged Access

FREE EBOOK
Cybersecurity for Dummies



