2021 Global State of Least Privilege Report

Erin Duncan
New Global Survey Reveals Why 20% of Organizations Fail When Implementing Least Privilege Cybesecurity
Delinea (formerly Thycotic) partnered with Cybrary, the cybersecurity workforce online training platform, to conduct a global survey of IT professionals focusing on how organizations are implementing a least privilege strategy. A new report summarizing the survey results reveals important insights for anyone planning or already down the path with their own least privilege security program.
2 out of 3 organizations now consider least privilege a top priority
The 2021 Global Cybersecurity Survey Report indicates that two out of three organizations now consider least privilege a top or urgent priority. Yet, many still struggle with trying to eliminate or restrict overprivileged users and the risks they pose.
And now that many more companies are managing remote workforces, it’s imperative that organizations accelerate their efforts to enable a “zero trust” risk model with least privilege security.
What is driving least privilege?
According to the survey, the reasons organizations are implementing least privilege are varied, with more than a third of respondents saying threats from employees and third parties are their main driver. That’s followed by more than one-fifth who indicate compliance is the main force behind their least privilege efforts.
Conducted in February, the survey likely does not reflect the vast expansion of endpoints that organizations must manage as the security perimeter disappears and many more are working remotely. This is especially concerning for IT staff with privileged access working from home along with employees using remote devices that may have local admin privileges. A single compromised endpoint with admin rights gives an attacker or malicious insider the means to elevate privileges and gain complete network access undetected.
Still lagging in least privilege common sense practices
Perhaps one of the most cautionary results from the survey reveals that 27% of respondents are sharing the same local administrator credentials on each machine—and another 20% still allow local administrator access on all employee accounts. Thus, among survey respondents, far too many are violating some of the basic principles and best practices of a least privilege security strategy.
Removing local administrative privileges on endpoints, for example, allows organizations to reduce their attack surface, thereby blocking a primary attack vector and preventing most breaches from occurring.

Least privilege initiatives that hamper user productivity increase the risk of failure
The continued persistence of overprivileged users might be explained by the pressure on IT departments to keep users working despite the risks. However, implementing least privilege by removing most or all user privileged access can create immediate pushback. According to the survey, 20% of respondents have already tried and failed to implement a least privilege initiative.
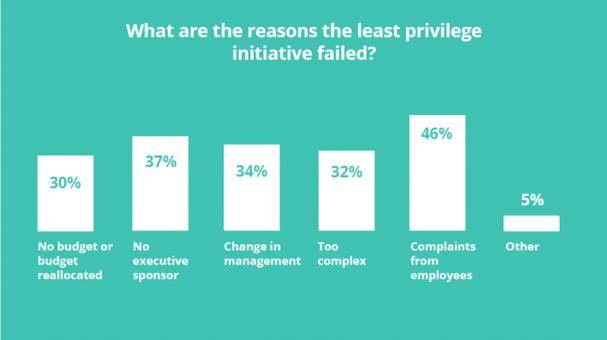
Among those failed least privilege efforts:
- 46% said user complaints were the biggest reason for least privilege failure
- 37% cited lack of executive sponsorship for failure
- 34% stated a change in management as a cause of failure
- 32% indicated complexity as the main reason their least privilege strategy failed
- 30% listed no budget or budget reallocation as a cause of failure
The survey report provides several useful recommendations for anyone involved in a least privilege initiative. When planning a least privilege strategy, security and identity teams need to engage with all employees. And when taking away end users’ permissions on their machines, IT needs to ensure they can still run the applications they need. Organizations can’t afford to sacrifice usability for security. Fortunately, there are Privileged Access Management (PAM) software solutions that can ensure least privilege with application control that minimizes any negative impact on business productivity.
What’s the best least privilege solution? It’s complicated.
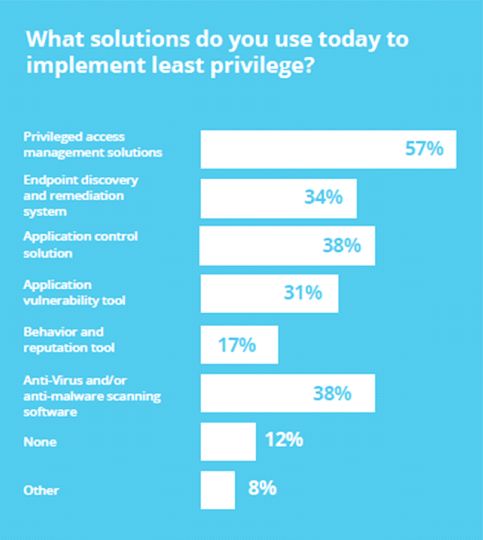
Because of the diverse and complex nature of IT environments today, survey respondents have deployed a wide range of technology solutions to implement least privilege. PAM is by far the preferred approach favored by 57% of the survey respondents, followed by application control solutions and anti-virus and anti-malware scanning software both at 38%.
Given that most operate in highly complex IT environments with hundreds if not thousands of users, applications, and services all needing privileged access, least privilege must be treated as an ongoing program, not a one-time cybersecurity project. It’s the only way to truly protect against internal and third-party threats and meet compliance mandates.
Least privilege, therefore, requires a multi-technology, multi-discipline approach. One that involves IT and security stakeholders collaborating with all parts of the organization. It should be supported by an executive who is responsible for security—CISO or VP-level security executive—who serves as the final decision maker, approves staff roles, and ensures an adequate budget is allocated.
The report recommends designating a “least privilege champion”—someone who recognizes the need for the program and solutions being implemented and who has a general security role with responsibility for identity and access management. This champion should also be the point person to communicate and coordinate with other influencers and stakeholders in the process, such as network security, application security, and other endpoint-related departments.
Conclusion: one size does not fit all
At a time when we are experiencing a record number of people required to work remotely, it’s imperative that organizations use all the tools at their disposal to enforce least privilege while maintaining user productivity.
Effective implementation of least privilege, especially on endpoints, requires multiple layers of protection. Existing solutions can and should be used in conjunction with a PAM product that provides least privilege-specific capabilities. Integration of these tools is necessary to help automate the task of ongoing management of a least privilege program. For example, your application control solution should connect to your IT help desk ticketing system, and work in conjunction with a vulnerability scanner.
There is no one product or one company that will meet all organizational needs for least privilege. A defense-in-depth strategy is key, in addition to integrating products that complement each other.
To see the survey results, get key takeaways and recommendations along with free resources, download the free 2021 Global State of Least Privilege Cybersecurity report here.
Implementing Least Privilege shouldn't be hard



