How to remove admin rights without reducing productivity

Joseph Carson
This is a guide to the risks associated with admin rights and over-privileged users, and how to remove admin rights in order to reduce those risks. There are many options for removing administrator rights, however, you must always consider business operation—removing admin rights should never jeopardize productivity.
Why do organizations use admin rights in the first place, and why remove them?
The reason administrator permissions are so freely granted is that it’s the easiest way to ensure end users can perform their jobs without involving IT. However, the security risks that come with having over-privileged users are high. You must either remove administrator rights to maximize security and maintain compliance or better manage administrator accounts on your systems to reduce the risk of them being abused.
The solution lies in removing admin rights and embracing the principle of least privilege (PoLP.)
In this short video, explain how to remove admin rights without compromising productivity:
The first step to removing admin rights is knowing where they are.
In Microsoft Windows you can simply type in the command prompt: “Net Users”
This was first introduced in Windows Vista and enables the administrator to add or modify user accounts, or displays user account information. This is how you can discover which administrator users and groups are on a single system.
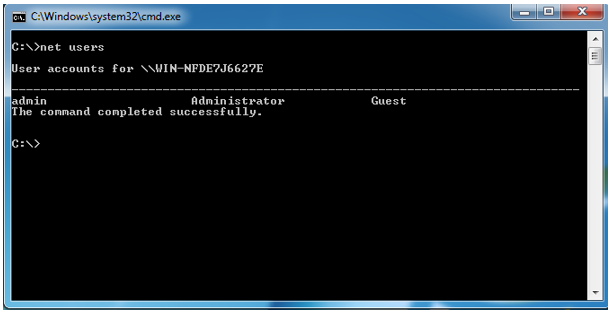
Net Users without any parameters will show the user's accounts available on the system.
Net localgroup adds, displays, or modifies local groups. Used without parameters, net localgroup displays the name of the server and the names of local groups on the computer.
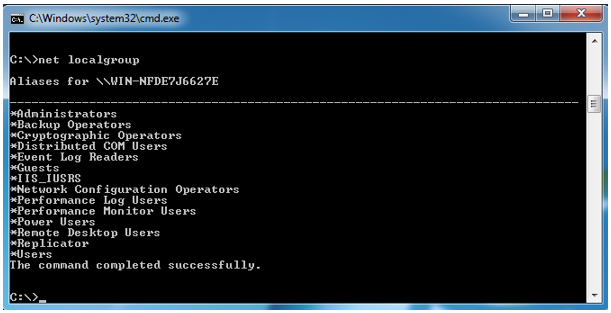
net localgroup displays the name of the server and the names of local groups on the computer.
Then using “Net localgroup Administrators” will display the members of the local administrator group.
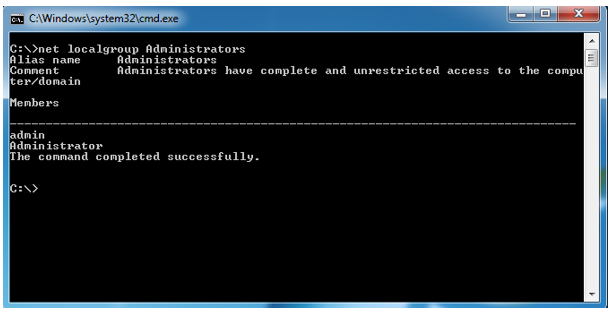
Using “Net localgroup Administrators” will display the members of the local administrator group.
Not everyone likes to use the command prompt, so Windows provides an easy way to visualize the net user and net localgroup output into a GUI.
This is known as Computer Management and can be launched by either typing in “Computer Management” or “compmgmt.msc” which will launch the window below. The folder named Local Users and Groups is where you can manage all local users and local groups.
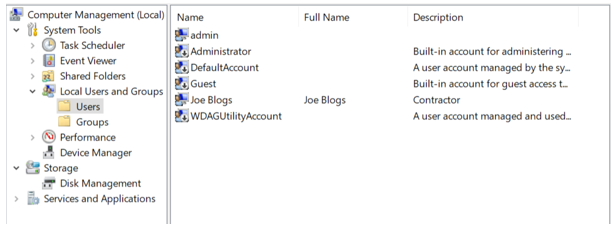
Computer Management
This works fine when you want to discover and remove admin rights from a single computer system. However, there are many tools and options that enable you to do this on a much larger scale. You will need to be able to discover all administrator rights across all your systems.
In the past, I would have scripted this or used WMI (Windows Management Instrumentation) to get the list from a larger number of systems.
You could also use Active Directory or Group Policy to force restricted groups or group membership so that local admin groups are strictly defined and any misconfigurations or modifications that are not approved are removed once the policy is refreshed.
How to discover admin rights on multiple systems
Delinea offers an easy-to-use free tool to help you discover where users have local admin rights.
It provides a detailed report to help you get started:

See which IT systems and users have higher privileges than they need
Using the Least Privilege Discovery Tool you can discover local admin accounts, service accounts, and applications in use on your endpoints.
- Find out which endpoints and local users have admin rights.
- Know what applications are in use and if they require admin rights to run.
- Get a comprehensive summary report highlighting your risks for local and service accounts and applications
Now, before you remove those admin rights
As I mentioned before you do not want to impact employee productivity by going and removing admin rights from all of those that you have discovered. You want to know:
- Who is actively using admin rights
- Which Applications require admin rights
- Which employees or developers install software frequently
- Who is using legacy applications
Make sure you balance security and productivity as effectively as possible. This is where Application Control can help you by creating policies that enable employees to perform the actions listed above at the same time without requiring admin rights.
IMPORTANT NOTE:
Removing admin rights from any executable that is launched requiring admin rights will prompt for the User Account Control (UAC) GUI. This was protection introduced in Windows Operating Systems to prevent users from making unauthorized changes or from accidentally clicking on malicious applications that infect systems.
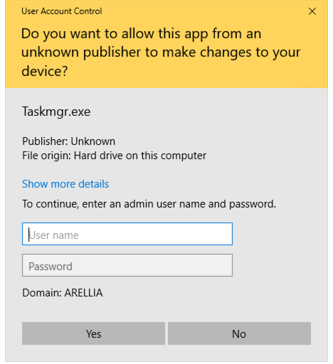
User Account Control (UAC) GUI
Application Control lets you remove admin rights while preserving productivity
Application control allows you to control privileges by elevating individual user accounts or by elevating applications.
Control privilege by elevating individual user accounts
This approach briefly elevates a user to a local admin or uses a hidden admin user stored on the endpoint when rights are required for applications or processes. This method creates vulnerabilities in your attack surface. Having an administrative end-user on an endpoint for even a few minutes can lead to catastrophic data breaches if the endpoint is compromised. Although the window of opportunity is small, cybercriminals don’t need long to get inside.
Control privilege by elevating applications
This approach elevates applications so that certain processes are allowed under certain pre-determined conditions. This method offers the strongest level of security by far because it ensures your users are NEVER operating as administrators. It is also the most scalable and sustainable strategy to maintain least privilege as your organization grows, individuals change roles, and business needs dictate new types of applications and processes.
Finally, check out Delinea’s solution to application control: Privilege Manager
Implementing Least Privilege shouldn't be hard



