New ransomware model presumes honor among thieves

Joseph Carson
ansomware is now big business, part of a production line of organized cybercrime. Thanks to ransomware’s new “affiliate” model, not only are attacks increasing in frequency, but they’re also becoming more sophisticated, successful, and damaging.
This new affiliate model is also known as Ransomware-as-a-Service
Ransomware attacks have victimized multiple organizations including TV stations, airplane manufacturers, and critical infrastructure, including Colonial Pipeline that recently caused gas shortages and panic buying. These are some prime examples of this new affiliate model, also known as Ransomware-as-a-Service—or RaaS.
Ransomware attacks have become so common, all organizations must be prepared to address them. Your ransomware strategy is critical to reducing the risk of a successful attack and shutting down ransomware progress before it shuts you down.
What is Ransomware-as-a-Service?
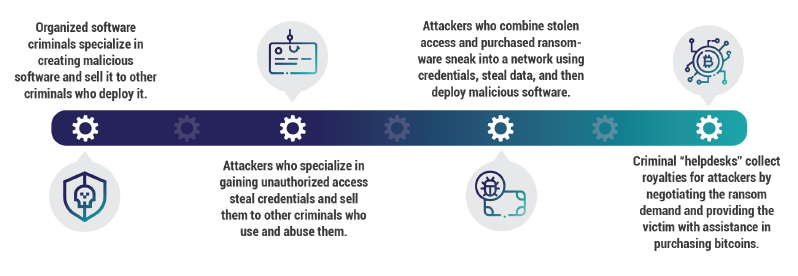
For Ransomware-as-a-Service to be successful, multiple parties are required to play different roles.
Creators of ransomware software, such as Darkside, make it available to a network of cybercriminals.
The criminals target victims and deploy ransomware. They collect the ransom from their targets and then provide a percentage of the ransom back to the original ransomware creator. They may also employ criminal “helpdesks” to collect royalties by negotiating the ransom demand and providing the victim with assistance in purchasing bitcoins or other popular cryptocurrencies.
Ransomware is now a big business, part of a production line of organized crime:
In this model, the creator of the ransomware has broader opportunities for success with minimal risk. If one affiliate is detected or ransom isn’t paid, there are many other opportunities to make money. The downside, of course, is that all partners need to play their role and not inform on or lead a trail back to the others. This means that ransomware becomes more targeted to avoid too much attention.
No organization is immune from becoming a ransomware victim
Organizations of all sizes can become a victim of ransomware. Larger organizations report a greater prevalence of attacks, with 42% of organizations with 1,001-5,000 employees admitting to having been hit, compared with 33% of smaller companies. In fact, the ransomware affiliate model encourages criminals to target large organizations and ask for bigger and bigger bounties, as they’ll only receive a percentage of the reward.
Ransom demands can reach tens of millions of dollars. Recent attacks on critical infrastructure, healthcare organizations, and local governments have caused so much disruption they have even put people’s lives at risk. A ransomware attack—even an unsuccessful one—likely requires investigations from regulators and invites legal action from customers and other stakeholders.
Video: Watch my RSA Conference talk on a real-world ransomware attack
Go beyond traditional, network-based cybersecurity solutions
A business user may be reading emails, opening documents, browsing the internet, clicking on links, or plugging in a USB device. If that user has unmanaged local administrator rights on their workstation, they can install and execute any application, no matter how they obtained the installation executable. When an attacker takes over that users’ workstation, it means they can, too. They can quickly install infectious or malicious tools to gain access to the rest of your organization.
A breach of a single system doesn’t have to allow an attacker unfettered privileged access to an entire IT environment. Network segmentation, threat detection solutions, and Privileged Access Management (PAM) are vital security solutions to prevent the ease of pivot building and lateral moves across your network.
At a minimum, all organizations should adopt the best practices and security approaches which the Cybersecurity and Infrastructure Security Agency (CISA), the U.S. federal agency responsible for securing the nation’s cybersecurity and communications infrastructure, and the Multi-State Information Sharing and Analysis Center (MS-ISAC) recommend in order to combat ransomware.
As attackers become more sophisticated, your strategies must continually evolve. In addition to the baseline recommendations put forth by CISA and MS-ISAC, Delinea’s new whitepaper, Ransomware on the Rise, outlines enhanced steps you can take to reduce risk by applying Privileged Access Management best practices and solutions to combat ransomware.
No matter how many preventive controls you put in place to block malware, there’s still a chance that sophisticated criminals will find ways into your organization. To reduce the risk of business disruption, you need to fortify your mitigating controls and put a ransomware incident response plan in place now.
How to become more resilient to ransomware
Ransomware attackers typically steal privileged credentials to infect as many systems as possible, including digital backups. They shut down critical systems, bringing a business to a complete stop. Once an organization is at its mercy, attackers typically threaten to release confidential information or corrupt data unless they’re paid a ransom.
You must detect when these activities are occurring so you can reduce the breach ‘dwell time’
You need to detect when these types of activities are occurring so you can reduce the breach's “dwell time.” This is the period before an attack is detected; a time in which the attacker may have gained access, avoided detection, stolen data, and left without a trace.
Traditional cybersecurity solutions have failed to prevent ransomware from infecting organizations and creating create mass disruption. Conventional signature-based antivirus programs are unable to prevent and detect these types of attacks due to the unique and quickly growing variants of ransomware. Encrypting your data doesn’t necessarily deter ransomware attacks either. Attackers may still threaten to publicly disclose that data, expecting that others are willing to pay for the opportunity to break the encryption.
Read Ransomware on the Rise: How to Reduce Risks and Respond to Attacks to learn how to make your organization stronger.
Finally, listen to our 401 Access Denied Podcast: Ransomware Rundown with Dan Lohrmann: