The Privileged Access Management lifecycle and path to maturity

Joseph Carson
Privileged Access Management (PAM) can be defined as managing privileged accounts and delegating privileged actions. Within an organization, it governs who can access or use a privileged account and what they can do once logged in with that privileged account. Privileged Access Management includes both privileged account management and privileged session management.
The PAM process has a well-defined lifecycle and 4 distinct phases of maturity that organizations typically pass through on their way to becoming what I call “PAM leaders”.
Let’s take a quick look at cyber threats, the enterprise, and PAM
Like me, you’re probably concerned about the ever-evolving threat landscape of cyberattacks as you watch large well-known enterprise organizations falling victim to cybercrime. Every year billions of records are stolen, identity theft increases, more credentials are abused, and financial fraud is now extending into billions of dollars.
Senior executives are more involved in cybersecurity than ever before. Even while executives and CISOs are trying to reduce the risk of these threats, compliance requirements are increasing, and the costs involved in helping their organizations stay protected and continue seamless operations are going up. Technology alone is no longer enough to defend organizations against cybercrime. Now, a strong defense must involve people, and therefore it needs to be simpler and quicker to value.
Why is traditional cybersecurity not enough?
Unfortunately, traditional cybersecurity is no longer sustainable. It is too complex, often too difficult to manage, and as a result, too costly—both in time and money. Therefore, organizations have little choice but to accelerate the move to simpler solutions; solutions that remove complex management demands on IT staff while at the same time building in more secure, seamless integrations.
Privileged Access Security is now one of the top security controls that many CISOs prioritize to help them reduce the risks of cyberattacks, empower their employees, and protect their organizations from unauthorized access. Gartner stated in 2018 that the #1 project to implement is Privileged Access Management. This still holds true today.
Your previous experiences with PAM Vendors may have been SCARY
Your previous experiences with legacy Privileged Access Management solution vendors may have been unnerving: the project may have been complicated, required expensive experts, been very costly, taken years to implement, or the software never got fully installed.
Delinea has made Privileged Access Management friendly. Our solution is simple and easy to use, can be easily learned by your own professionals, and provides value for money. Implementation is a fast and satisfying experience.
What’s the best way to get started with Privileged Access Management?
Now, the problem for many organizations is where to start the PAM journey. How do you easily adopt a privileged access solution into your organization that will lead you to success and maturity? Delinea has developed a selection of resources to help educate you and get you started immediately without any cost.
Organizations that are just getting started with protecting and securing privileged access must identify which privileged accounts should be targeted. They must also ensure that those who will be using those privileged accounts are clear on the acceptable use and responsibility.
Start by defining what ‘privileged access’ means in your organization
How to define what ‘privileged access’ means in your organization
Before implementing a Privileged Access Management plan you must identify what a privileged account is for your organization. It’s different for every company so it is crucial you map out what important business functions rely on data, systems, and access.
A useful approach is to simply re-use your disaster recovery plan which typically classifies important systems that need to be recovered first, and then identify the privilege accounts for those systems. Classifying or categorizing privileged accounts at this stage is good practice as this helps identify your privileged accounts’ importance to the business and will make future decisions easier when it comes to applying security controls.
So, what does privileged access mean in your organization? It could mean access to infrastructure, sensitive data, configuring systems, deploying patches, scanning for vulnerability, cloud environments, and a lot more. To be able to achieve a solid definition I recommend you perform a Data Impact Assessment because this is exactly what most privileged accounts are protecting and used for—to access sensitive data or enable access to sensitive data.
Once you have conducted a Data Impact Assessment to classify your data, you’ll know what information is most important to your business.
Next, audit and confirm who should have access rights to view and manage this sensitive data.
Privileged accounts are everywhere—yet for most people they are invisible
Privileged accounts are everywhere in the IT environment. They are the glue that connects vast information networks. Yet for most people they are invisible.
Privileged accounts can be human or non-human. Some privileged accounts are associated with individuals such as business users or network administrators, while others are application accounts used to run services and are not associated with a person’s unique identity.
Now, you can follow the PAM Lifecycle
Once you have performed a Data Impact Assessment and confirmed who should have access rights, the next step to maturity is to follow the Delinea Privileged Access Management Lifecycle. This will get you moving quickly on the path to protecting and securing privileged access. You can learn more about the Privileged Access Management Lifecycle in Delinea’s free PAM for Dummies eBook.
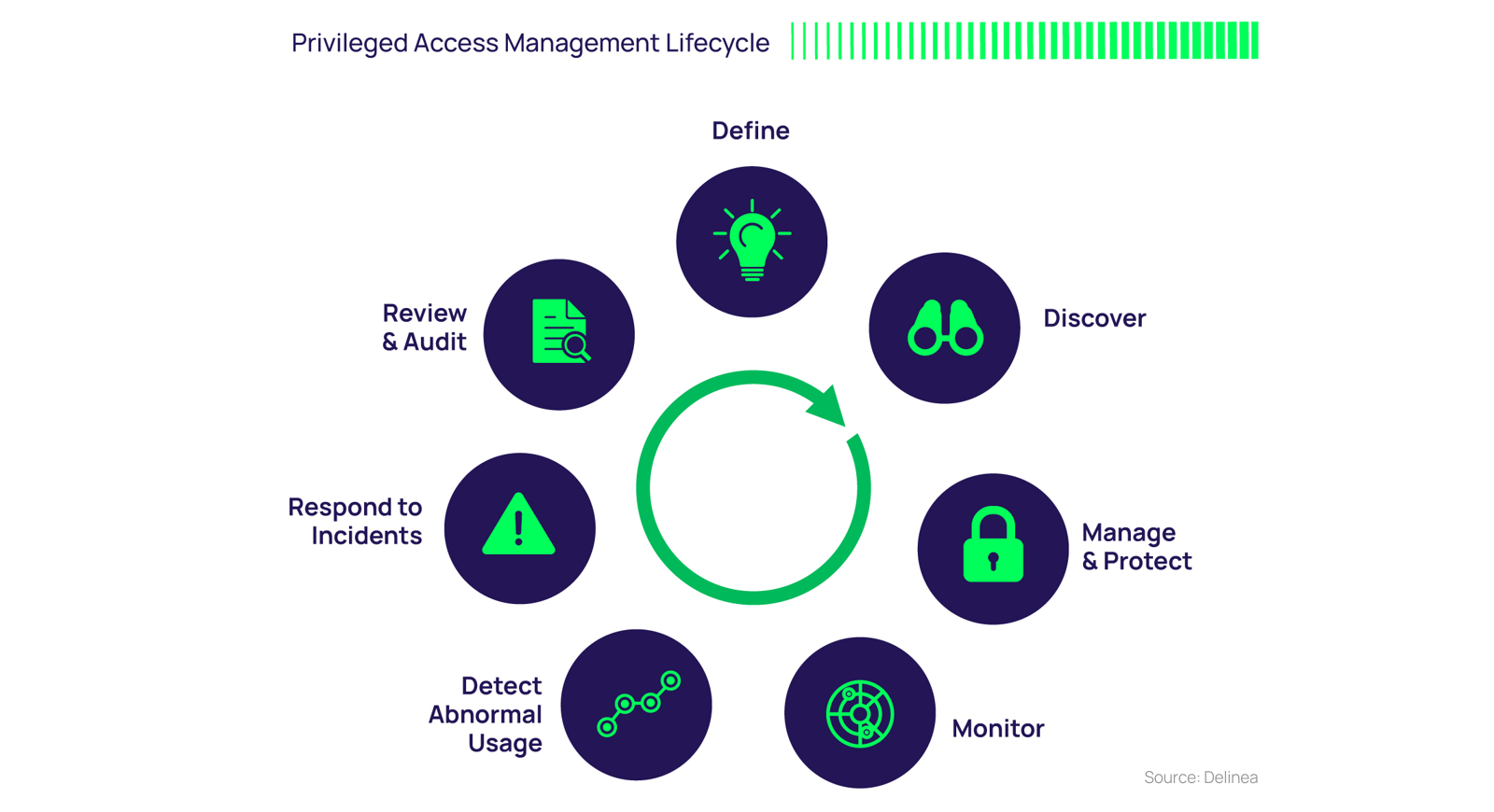
Like any IT security measure designed to help protect critical information assets, managing and protecting privileged account access requires both a plan and an ongoing program. You must identify which privileged accounts should be a priority in your organization, and ensure that those who are using these privileged accounts understand acceptable use and their responsibilities.
Here are the steps of the PAM Lifecycle:
1. Define
Define and classify privileged accounts. Your business functions rely on data, systems, and access, and dependence on these entities varies from one organization to another. If you’re unsure how to start this task, look at your disaster recovery plan as it typically classifies your critical systems. Then, don’t forget to align your privileged accounts to your business risk and business operations.
Develop IT security policies that explicitly cover privileged accounts. Does your organization have a policy that details acceptable use and responsibilities for privileged accounts? You must have a working understanding of who has privileged access, and when it is used. For this reason, you must treat privileged accounts separately by clearly defining a privileged account and spelling out acceptable use policies.
2. Discover
Discover your privileged accounts. Automated Privileged Access Management software enables you to identify your privileged accounts, implement continuous discovery to curb privileged account sprawl, identify potential insider abuse, and reveal external threats. This full, ongoing visibility of your privileged account landscape is central to combating cybersecurity threats.
3. Manage and protect
Protect your privileged account passwords. Proactively manage, monitor, and control privileged account access with password protection software. Verify that your password management solution can automatically discover and store privileged accounts; schedule password rotation; audit, analyze, and manage individual privileged session activity; and monitor password accounts to detect and respond to malicious activity quickly.
Limit IT admin access to systems. Develop a least privilege policy to enforce least privilege on endpoints without disrupting business operations. Privileges should only be granted when required and approved. The least privilege and application control solutions enable seamless elevation of approved, trusted, and allowed applications while minimizing the risk of running unauthorized applications.

Need a step-by-step guide for planning your strategic journey to privileged access security?
4. Monitor
Monitor and record sessions for privileged account activity. Your Privileged Access Management solution should be able to monitor and record privileged account activity. This helps enforce proper behavior and avoid user mistakes because they know their activities are being monitored. In the event of a breach, monitoring privileged account use also helps digital forensics identify the root cause and identify critical controls that can be improved to reduce your risk of future cybersecurity threats.
5. Detect abnormal usage
Track and alert on user behavior. Up to 80% of breaches involve a compromised user or privileged account. Do not underestimate the value of gaining insights into privileged account access and user behavior. Visibility into the access and activity of your privileged accounts in real-time helps catch suspected account compromise and potential user abuse. Behavioral analytics focuses on key data points to establish individual user baselines, including user activity, password access, similar user behavior, and time of access to identify and alert on suspicious activity.
6. Respond to incidents
Prepare an incident response plan in case a privileged account is compromised. Simply changing privileged account passwords or disabling the privileged account is not adequate when a privileged account is breached. Once in your system, cyber criminals can install malware and even create their own privileged accounts. If a domain administrator account gets compromised, for example, you should assume that your entire Active Directory is also compromised.
How to prepare an incident response plan:
Check out our Cyber Incident Response Checklist
Download our free Incident Response Plan Template
7. Review and audit
Audit and analyze privileged account activity. Continuously monitoring privileged account usage via audits and reports helps identify unusual behaviors. This may indicate a breach or misuse. These automated reports aid in tracking the cause of security incidents, and also demonstrate compliance with policies and regulations. Additionally, privileged account audits equip you with the appropriate cybersecurity metrics and vital information organization an executive requires to make more informed business decisions.

Where are you in your PAM maturity journey?
The bottom line
The key to improving cybersecurity around Privileged Access Management stems from an understanding and implementation of a PAM lifecycle approach. Only a comprehensive solution can ensure that your “keys to the kingdom” are properly protected from cyber criminals and malicious insider threats. And that your access controls meet your industry's regulatory requirements for compliance mandates.
Privileged access and the latest cybersecurity methods:
In this video, Delinea’s Chief Security Scientist and author of “PAM for Dummies,” Joseph Carson, delves into privileged access and the latest cybersecurity methods and explains why you cannot approach cybersecurity from a technology-only point of view.



