Cybersecurity Incident Response Plan Template

Joseph Carson
Since we first published our customizable cybersecurity incident response plan template, I’ve been amazed by the number of people who downloaded it. It’s hands down one of Delinea’s most popular templates.
In this blog, you'll find all the information you need to get started with your Incident Response Plan and Strategy:
What is in the incident response plan template?
Maintaining your incident response plan
FAQS: Communicating your plan with the rest of the organization
The difference between incident response and incident handling
What is the incident response life cycle?
What are the different types of information security incidents?
Industry-specific incident reporting
Cyberattacks lurk as a constant danger, poised to disrupt businesses without warning. Robust incident response plans, refined through testing, are crucial to withstand inevitable threats and build cyber resilience.
New SEC rules require public companies to disclose cyber incidents that result in a material impact on the business, which also makes incident response planning essential, and regulations demand rapid and frictionless reporting.
If you’re ready to build an incident response plan but not 100% sure what it must include, this template is a great place to start. Based on best practices and hands-on experience from cyber practitioners, the template sets the foundation for an incident response strategy that’s proactive, pragmatic, and simple to adopt.
Let’s take a closer look at what’s inside the incident response plan template, and then I’ll address some commonly asked questions about incident response that will help you build awareness in your organization.
What’s in the incident response plan template?
Action steps included in the template focus on the importance of protecting privileged accounts to prevent a cyberattack from escalating. When privileged accounts are compromised, the potential impact of a breach increases, as does the time it takes to identify, contain and stop the attacker. In the template, we have prioritized actions that help you discover and contain privileged access attacks quickly and effectively while maintaining business continuity.
The plan coordinates the efforts of everyone in your organization involved in incident response and explains the different roles, including:
- Security leaders
- Operations managers
- Business leaders
- Help desk teams
- Identity and Access (IAM) managers
- Audit and compliance teams
- Legal teams
- Communication teams
- Executives and Board members
The incident response template also has the following content:
- Guidance on assembling an incident response team, including IT, compliance, and communications representatives
- Appropriate actions to take during each phase of a cyber incident
- A sample incident scenario you can use for tabletop exercises and training
The template structure :
We’ve structured the template to make sure you cover all the important steps in the right order, from ownership to eradication and lessons learned, including:
- Defined ownership and approval
- Immediate mitigation actions
- Roles, responsibilities, and updated contact information
- Compliance requirements
- Threat classification/risk severity
- Legal and reporting obligations
- Record of decision-making and actions taken
You can customize the incident response plan template to document your own team members, requirements, priorities, and action steps.
Tips for maintaining your incident response plan:
Your incident response plan isn’t a one-and-done activity. You and your team should review it regularly and evolve the plan to align with changes in your organizational structure, risk profile, supply chain relationships, and anything else that could impact the way you’ll want to respond to cyber incidents.
- Practicing your incident response plan is just as important as having a fire drill. Test your plan with realistic dry runs until you’re confident that your process will flow as planned. Have practice runs after significant changes to your IT or organizational environment. The best incident response plans are the ones that have been tested and simulated.
- Walk through the plan as part of the onboarding process for relevant new hires.
- Update and review your incident response plan template on a schedule, perhaps quarterly.
Is this incident response plan template right for my company?
There are many companies who think they’re too small to need a plan, or even too small to be targeted by an attacker. They may also worry that they don’t have the staff to manage an incident response plan. This couldn’t be further from the truth. Even the smallest organizations are at risk from cyberattacks and benefit from documenting an incident response plan before an incident occurs.
If you’re an IT leader who’s also responsible for cybersecurity, incident response may not be something you think about every day. You may need to deputize people to play roles outside of their comfort zone. Even more reason to document and practice.
Some companies rely on third parties to support their incident response activities. If that’s you, you’ll want to be sure you and your vendor use shared documents, such as this incident response plan template, to make sure you’re on the same page.
Incident Response FAQ: communicating your plan with the rest of the organization
Now that we’ve walked through the incident response plan template, let’s address some frequently asked questions about incident response. As you roll out your incident response plan to your organization, chances are that folks who aren’t as familiar with the topic will need some background to understand its importance.
Below are some explanations you can share to build awareness and gain their support.
1. What is incident response?
Incident response is an organization’s reaction to a cybersecurity incident, such as a data breach or ransomware attack.
Cybersecurity has both a technical AND a human element.
Cybersecurity involves security controls and activities that require coordinated efforts across IT operations and security teams. These activities include discovering and containing attacks, as well as backup, recovery, and digital forensics. In addition, cybersecurity includes outbound activities such as communication with partners and customers and reporting to regulatory authorities and cyber insurance companies.
The goal of having an incident response plan is to ensure that your organization is fully prepared for, and ready to respond to any level of cybersecurity incident quickly and effectively. It’s a key part of a risk management program and business resiliency.
2. Is there a difference between incident response and incident handling?
Well, yes, although response and handling go hand in hand, and without both, you do not have a sound incident response process.
- Incident response refers to the technical aspects of incident analysis and containment
- Incident handling refers to the human responsibilities: the communications, coordination, and cooperation required to see the process through.
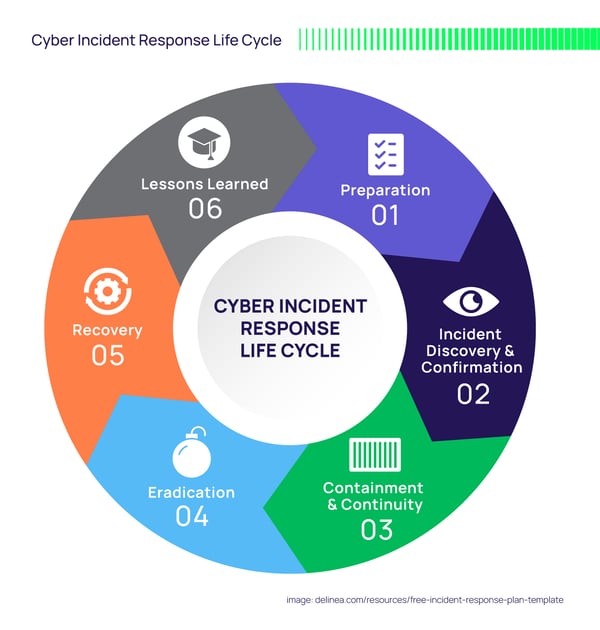
3. What is the incident response life cycle?
The lifecycle of a cybersecurity incident is defined by the stages a typical incident goes through, and it includes everything from preparing for an incident to analyzing the lessons you learned after experiencing one.
I’m quite partial to this version of the incident response life cycle: Preparation > Incident Discovery and Confirmation > Containment and Continuity > Eradication > Recovery > Lessons Learned
4. What are the different types of information security incidents?
There are many types of cybersecurity incidents that can result in intrusions on your organization’s network or full-on data breaches, but I’m going to focus on the six to which I believe organizations are most vulnerable:
Phishing attacks: you click on a link in an authentic-looking email and end up giving away sensitive information (like a password) or enabling ransomware or some other malware. Companies are super-vulnerable to phishing attacks because cyber criminals target employees and abuse their trust—and success rates are high! Spearfishing is a more targeted type of phishing attack that occurs when the attacker invests time researching the victim to pull off an even more successful attack.
Denial-of-Service (DoS) attacks: the point of this attack is to shut down an individual machine or entire network so that it cannot respond to service requests. DoS attacks achieve this by inundating the target with traffic or sending it some information that triggers a crash.
Man-in-the-Middle (MitM) attacks: I prefer to call these Person-in-the-middle (PitM), which is when an outside entity intercepts and alters the communication between two parties who believe they are communicating with each other. By impersonating them both, the attacker manipulates both victims to gain access to data. The users are blissfully unaware that they are both talking to an attacker. Session hijacking, email hijacking, and Wi-Fi eavesdropping are all examples of PitM attacks.
Drive-by attacks: a common method of spreading malware, cyber criminals seek out insecure websites and plant a malicious script into code on one of the pages. The script could install malware onto the computer of someone who visits the site or re-direct the victim to a different site controlled by cybercriminals.
Password attacks: this sort of attack is aimed specifically at obtaining a user or an account’s password. Cybercriminals use a variety of techniques for getting their hands on passwords, such as password-cracking programs, dictionary attacks, password “sniffers”, or brute-force password guessing, often based on some personal knowledge of an individual (birthday, dog’s name, etc.) This is why strong passwords are so important.
Malware and ransomware attacks: a broad term for any sort of malicious software that’s installed on your system without your consent can be considered malware. You’re probably familiar with many types of malware—file infectors, worms, Trojans, ransomware, adware, spyware, logic bombs, and different types of viruses. Some are inadvertently installed when an employee installs freeware or other software, clicks on an ad, or visits an infected website.
The possibilities are endless; therefore, so are the chances of an employee falling victim to a malware attack. Download our free Ransomware Defense Toolkit to learn best practices in becoming more resilient so you can avoid being a ransomware victim.
5. What is industry-specific cybersecurity incident reporting?
The incident response process described in the lifecycle above is largely the same for all organizations, but the incident reporting procedure varies for certain industries. For example, if you’re in the healthcare industry you may need to observe the HIPAA incident reporting requirements.
Here are some industry regulations that have very specific laws around incident reporting, and to whom they apply:
HIPAA – if you create, receive, maintain or transmit electronically protected health information
FISMA/NIST – if you’re a U.S. Federal agency or government contractor
PCI DSS – if you accept, store, or transmit credit card data
NERC/CIP – if you’re an energy and utility company
SOX – if your organization is a public company (though in some cases, private companies must also comply with SOX regulations)
NYCRR – if you’re a New York insurance company, bank, or other regulated financial services institution
If your organization must adhere to any of the above regulations, you must familiarize yourself with the incident reporting requirements that may uniquely apply to your industry and customize your template accordingly. Links to helpful industry-specific information can be found in the incident response plan template.
As an additional resource, our whitepaper “How to Build Your Incident Response Plan” provides a broader incident response strategy.
Incident response is a plan I hope you’ll never need
I talk about the incident response process often, but always with the hope that you’ll never need to report an incident.
No solution you choose to protect your privileged access, nor any amount of employee training, will guarantee you bulletproof cybersecurity. After all, the cybercriminal’s ongoing challenge is to stay a step ahead of you. But having a rock-solid incident response plan in place can minimize the damage—even stop it before it gets a foothold—and protect your money, time, and reputation.
As more organizations take steps to protect themselves, become more resilient, and recover quickly, I look forward to seeing a future with fewer victims of cybercrime.




